Category:Open DNS Resolvers: Difference between revisions
No edit summary |
m (update clueless to control) |
||
| (47 intermediate revisions by 4 users not shown) | |||
| Line 1: | Line 1: | ||
==What is an |
==What is an open DNS resolver?== |
||
Every day, |
Every day, each time we use DNS to look up names and IPs on the Internet - e.g. when you put bbc.co.uk in your browser, your computer needs to look up the IP address of the BBC's web server. To do this it will use DNS. The DNS server will respond back to your computer with the information. |
||
AAISP customers normally use the AAISP DNS servers, or often their own router. |
AAISP customers normally use the AAISP DNS servers, or often their own router. |
||
It is quite common for DSL routers to respond to these DNS requests on the WAN side as well as the LAN - this means that other people on the Internet can use your router to do their DNS |
It is quite common for DSL routers to respond to these DNS requests on the WAN side as well as the LAN - this means that other people on the Internet can use your router to do their DNS lookups. It also means that 'attackers' can take advantage of this and use your router to attack someone else. This will use up bandwidth on your line. |
||
The 'attack' in this sense is more about attacking somebody else on the Internet by using your DNS resolver. What happens is that an attacker sends a DNS request to your router from a spoofed IP address. This spoofed IP address is the IP that the attacker wants to target, the victim. Your router then replies to the spoofed IP address with the DNS result. The DNS reply is larger in size than the request, and thus this is an 'amplification' attack. On its own one router won't make a difference, but when the same amplification attack is applied to many routers the aggregate reply traffic can become quite disruptive to the victim. |
|||
| ⚫ | |||
<center> |
|||
| ⚫ | |||
{| class="wikitable" |
|||
!colspan="2"|DNS amplification attack diagrams |
|||
|- |
|||
|[[File:Opendns1.png|300px|DNS attack]] |
|||
|[[File:Opendns2.png|300px|Multiple attacks bring the victim down]] |
|||
|- |
|||
!Single attack to a victim |
|||
!By using multiple open servers, the attacker can bring the victim down by flooding it with traffic. |
|||
|} |
|||
</center> |
|||
| ⚫ | |||
| ⚫ | |||
==What if I run a DNS server on purpose?== |
==What if I run a DNS server on purpose?== |
||
| ⚫ | |||
| ⚫ | |||
| ⚫ | |||
If you run |
If you run a caching resolver, configure it to only return records for your users (firewall to only allow your users), and consider implementing rate-limiting. |
||
You can disable our automatic scanning, see [[#Disabling Automatic Scans]] below. |
|||
| ⚫ | |||
=How to |
=How to prevent this?= |
||
In short, a router with DNS open on the WAN side should have |
In short, a router with DNS open on the WAN side should have its DNS service disabled or fire-walled. (port 53 to the router should be blocked) |
||
See the pages below for details on specific routers |
See the pages below for details on specific routers |
||
=Automatic and Manual Testing for Open Resolvers= |
|||
There is a page on the AAISP control pages that lists your IPs that have an open DNS server running, and can also re-scan your IP blocks (IPv4). AAISP will re-scan automatically every so often and will alert customers by email if an open DNS resolver is found. Sorry, but we don't have enough time to scan IPv6 addresses. |
|||
Log in to the [https://control.aa.net.uk/ Control Pages], and then either click on one of your IPv4 addresses or a broadband line. On these pages you'll see a link to the open DNS page. |
|||
==Disabling Automatic Scans== |
|||
On a per IP block basis you can disable our regular scans. From the Control Pages, click on the IP block and change the setting. |
|||
[[File:DNS-Check-flag.png|border]] |
|||
You will still be able to run the checks manually. |
|||
[[Category: |
[[Category:Routers]] |
||
[[Category:DNS]] |
|||
[[Category:Diagnostic Tools]] |
|||
Latest revision as of 11:29, 7 November 2016
What is an open DNS resolver?
Every day, each time we use DNS to look up names and IPs on the Internet - e.g. when you put bbc.co.uk in your browser, your computer needs to look up the IP address of the BBC's web server. To do this it will use DNS. The DNS server will respond back to your computer with the information.
AAISP customers normally use the AAISP DNS servers, or often their own router.
It is quite common for DSL routers to respond to these DNS requests on the WAN side as well as the LAN - this means that other people on the Internet can use your router to do their DNS lookups. It also means that 'attackers' can take advantage of this and use your router to attack someone else. This will use up bandwidth on your line.
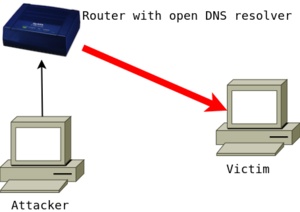
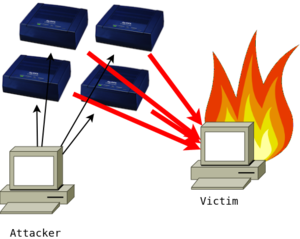
The 'attack' in this sense is more about attacking somebody else on the Internet by using your DNS resolver. What happens is that an attacker sends a DNS request to your router from a spoofed IP address. This spoofed IP address is the IP that the attacker wants to target, the victim. Your router then replies to the spoofed IP address with the DNS result. The DNS reply is larger in size than the request, and thus this is an 'amplification' attack. On its own one router won't make a difference, but when the same amplification attack is applied to many routers the aggregate reply traffic can become quite disruptive to the victim.
| DNS amplification attack diagrams | |
|---|---|
|
|
| Single attack to a victim | By using multiple open servers, the attacker can bring the victim down by flooding it with traffic. |
In the past having an open resolver on a router wasn't a problem, and there are many many routers which leave DNS open in their default state. However, this has been exploited and so it is best to disable this feature on routers.
This is often referred to as a 'DNS amplification attack'.
What if I run a DNS server on purpose?
It is quite legitimate for people to run DNS servers on their network, and we are happy for them to do so - in these cases access to them should be restricted or limited.
If you run an authoritative DNS server, configure it only to return records for your domain.
If you run a caching resolver, configure it to only return records for your users (firewall to only allow your users), and consider implementing rate-limiting.
You can disable our automatic scanning, see #Disabling Automatic Scans below.
How to prevent this?
In short, a router with DNS open on the WAN side should have its DNS service disabled or fire-walled. (port 53 to the router should be blocked)
See the pages below for details on specific routers
Automatic and Manual Testing for Open Resolvers
There is a page on the AAISP control pages that lists your IPs that have an open DNS server running, and can also re-scan your IP blocks (IPv4). AAISP will re-scan automatically every so often and will alert customers by email if an open DNS resolver is found. Sorry, but we don't have enough time to scan IPv6 addresses.
Log in to the Control Pages, and then either click on one of your IPv4 addresses or a broadband line. On these pages you'll see a link to the open DNS page.
Disabling Automatic Scans
On a per IP block basis you can disable our regular scans. From the Control Pages, click on the IP block and change the setting.
You will still be able to run the checks manually.
Pages in category 'Open DNS Resolvers'
The following 8 pages are in this category, out of 8 total.