FireBrick Road Warrior FireBrick Config: Difference between revisions
(Created page with "= FireBrick IPsec config = The FireBrick needs a configuration for the connection, and roaming pools and user identities. The connection can be used for any number of devices...") |
mNo edit summary |
||
| Line 32: | Line 32: | ||
</rule-set> |
</rule-set> |
||
</syntaxhighlight> |
</syntaxhighlight> |
||
[[Category:FireBrick_IPsec_Road_Warrior]] |
|||
Revision as of 15:41, 30 July 2015
FireBrick IPsec config
The FireBrick needs a configuration for the connection, and roaming pools and user identities. The connection can be used for any number of devices at once with the same pool of IP addresses; each would have a user name and password defined.
The basic server config is in ipsec-ike containing a connection and roaming entry, e.g.
<ipsec-ike>
<connection name="server" roaming-pool="roam-pool" auth-method="Certificate" peer-auth-method="EAP" mode="Wait" local-ID="FQDN:server.example.com"/>
<roaming name="roam-pool" ip="[ranges of LAN IPs]" DNS="[DNS, e.g. 8.8.8.8]"/>
</ipsec-ike>Each roaming user then needs an eap user record.
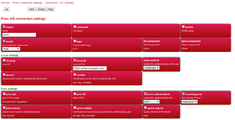
<eap name="fred" full-name="Fred Bloggs" password="[password]" subsystem="IPsec" methods="MSChapV2"/>Here is how the above three config sections look in the User Interface (UI):
- FireBrick SCreenshots
Firewall
You will also want to look at the Firewall on the FireBrick and allow traffic where required, for example, to Allow the IPsec users to connect to the Internet via your PPPoE connections use something like:
<rule-set name="FromIPSec" source-interface="ipsec" no-match-action="continue">
<rule name="AllowInternet" target-interface="pppoe" action="accept"/>
</rule-set>