FireBrick Road Warrior OSX: Difference between revisions
| Line 36: | Line 36: | ||
##Server address: IP or Name of your FireBrick |
##Server address: IP or Name of your FireBrick |
||
##Click OK |
##Click OK |
||
<gallery> |
|||
FireBrick_IPsec_OSX_Dalek.png|Add a Strongswan connection |
|||
FireBrick_IPsec_OSX_connection.png|Strongswan settings |
|||
</gallery> |
|||
==Connect!== |
==Connect!== |
||
Revision as of 16:33, 30 July 2015
It is possible to connect an Apple Mac with OSX to a FireBrick over IPSEC with IKEv2 and EAP. Regrettably the IPSEC facilities within OSX are not fully enough featured to achieve this alone, so some additional VPN client software can be installed called StrongSwan.
Downloading & installing the StrongSwan Native Client
Visit the download site and download the latest binary. At the time of writing the latest version was strongswan-5.2.2-1.app.zip. Allow the machine to unarchive it; usually by selecting the "Open with Archive Utility" option. This will deposit the StrongSwan.app into your downloads directory. Drag the app from the downloads directory into your Applications folder. This completes installation of the StrongSwan Client.
Getting the CA from the FireBrick
Note: this guide doesn't go into actual configuration of the FireBrick to be an endpoint, merely how to connect your Mac client to it. Therefore it is assumed the certificate already exists on the FireBrick. It may also be that this is emailed to you by whoever maintains your FireBrick, in which case skip this step.
- Log into the Firebrick.
- Click on the Config menu in the bar on the left.
- Click on the Certificates menu beneath that.
- You should be presented with a list of certificates installed. Each line will look approximately as follows :
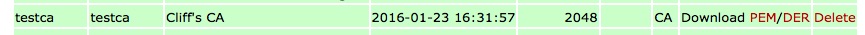
- At the right hand end of the row corresponding the the certificate you wish to download, click on the PEM link.
Installing the CA certificate into OSX
- Go to: Applications - Utilities - Keychain Access
- In the top/left area named 'Keychains, click on System
- In the bottom/left are named 'Category', click on Certificates
- Go to: File - Import Items
- Select the file you've downloaded, eg ca-cert.pem
- Review the certificate and then select Always Trust, you may be asked to confirm your apple user password.
Configure Strongswan
Run strong swan You'll have a swan icon in your clock tool bar at the top (it actually looks like a Dalek!)
- Click Add Connection
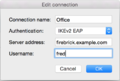
- Name: eg FireBrick
- Authentication IKEv2 EAP
- Server address: IP or Name of your FireBrick
- Click OK
Connect!
- Click on the
DalekStrongSwan icon once more, click your connection name then connect. - You'll be prompted for the password, this is the one as set up in the EAP Identity on the FireBrick (in this example, we had set up a user of fred with a password)
Errors/help
Unsupported integrity algorithm
There is one "gotcha" with StrongSwan on MAC though - it may negotiate an encryption algorithm for the data connection which OS X doesn't support, the FireBrick will create a log like:
failed to create ESP context: unsupported integrity algorithm AES_XCBC_96
This really a bug in the way the StrongSwan app was built - it shouldn't negotiate AES if the underlying OS can't do it (which as of July 2015 OSX can't manage AES). However, the easy workaround is to set up an ipsec-proposal to avoid this:
- On the FB config editor create a 'Proposals for IPsec AH/ESP security association'.
- Give is a name, and set, for example, HMAC-SHA1 for authset.
- Then, back in the 'IPsec IKE connection settings' select the new Proposal in the 'ipsec-proposals' drop down.
Here is example config for this:
<IPsec-proposal name="custom" authset="HMAC-SHA1"/>