FireBrick Road Warrior FireBrick Config: Difference between revisions
mNo edit summary |
|||
| Line 2: | Line 2: | ||
= FireBrick IPsec config = |
= FireBrick IPsec config = |
||
==Overview== |
|||
In this example we are assuming you can allocate some IP addresses on you LAN. You do this by picking a range of addresses and setting up a roaming-pool (see below). You need to ensure the IP range does not clash with devices on the LAN and is not in the DHCP ranges that could allocate to the LAN. |
In this example we are assuming you can allocate some IP addresses on you LAN. You do this by picking a range of addresses and setting up a roaming-pool (see below). You need to ensure the IP range does not clash with devices on the LAN and is not in the DHCP ranges that could allocate to the LAN. |
||
The FireBrick needs a configuration for the connection, and roaming pools and user identities. The connection can be used for any number of devices at once with the same pool of IP addresses; each would have a user name and password defined. |
The FireBrick needs a configuration for the connection, and roaming pools and user identities. The connection can be used for any number of devices at once with the same pool of IP addresses; each would have a user name and password defined. |
||
==Proxy ARP== |
|||
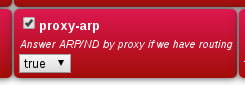
You also need to set proxy-arp on the LAN interface settings to allow communications to other devices on your LAN. Alternatively you could set private IP addresses in the pool and set the nat setting. You should probably also consider firewalling rules for traffic to/from IPsec connections. |
|||
[[File:FireBriickProxyARP.png|framed|none|Proxy ARP setting on the subnet]] |
|||
==Configuration== |
|||
The basic server config is in <tt>ipsec-ike</tt> containing a <tt>connection</tt> and <tt>roaming</tt> entry, e.g. |
The basic server config is in <tt>ipsec-ike</tt> containing a <tt>connection</tt> and <tt>roaming</tt> entry, e.g. |
||
Revision as of 09:32, 25 August 2015
FireBrick IPsec config
Overview
In this example we are assuming you can allocate some IP addresses on you LAN. You do this by picking a range of addresses and setting up a roaming-pool (see below). You need to ensure the IP range does not clash with devices on the LAN and is not in the DHCP ranges that could allocate to the LAN.
The FireBrick needs a configuration for the connection, and roaming pools and user identities. The connection can be used for any number of devices at once with the same pool of IP addresses; each would have a user name and password defined.
Proxy ARP
You also need to set proxy-arp on the LAN interface settings to allow communications to other devices on your LAN. Alternatively you could set private IP addresses in the pool and set the nat setting. You should probably also consider firewalling rules for traffic to/from IPsec connections.
Configuration
The basic server config is in ipsec-ike containing a connection and roaming entry, e.g.
<ipsec-ike>
<connection name="server" roaming-pool="roam-pool" auth-method="Certificate" peer-auth-method="EAP" mode="Wait" local-ID="FQDN:server.example.com"/>
<roaming name="roam-pool" ip="[ranges of LAN IPs]" DNS="[DNS, e.g. 8.8.8.8]"/>
</ipsec-ike>Each roaming user then needs an eap user record.
<eap name="fred" full-name="Fred Bloggs" password="[password]" subsystem="IPsec" methods="MSChapV2"/>Here is how the above three config sections look in the User Interface (UI):
- FireBrick SCreenshots
Firewall
There are two aspects to Firewalling:
- Allowing IPsec traffic in to the FireBrick
- Controlling what an IPsec client, once connected, has access to
Allow IPsec traffic in to the FireBrick
- See: IPsec_Firewall
Controlling client traffic
You will also want to look at the Firewall on the FireBrick and allow traffic where required, for example, to Allow the IPsec users to connect to the Internet via your PPPoE connections use something like:
<rule-set name="FromIPSec" source-interface="ipsec" no-match-action="continue">
<rule name="AllowInternet" target-interface="pppoe" action="accept"/>
</rule-set>DNS Servers
If you set the DNS servers in the pool to be the FireBrick's IP address then you will need to allow access. This will be done with:
- Firewal rules (port 53 to the FireBrick from IPsec
- Editing the DNS Service to allow non-local users, we'd recommend using an Allow list that includes the IPsec clients as well as the LAN clients if they are to also use the FireBrick as their DNS resolver. (Setup - General System Services - DNS)