PGP: Difference between revisions
Created page with "<indicator name="Front">link=Category:Technical Documents|30px|Back up to the Technical Documents category</indicator> ==Introduction== PGP (Prett..." |
m →Changing your key/passphrase: Minor cleanup |
||
| (2 intermediate revisions by 2 users not shown) | |||
| Line 13: | Line 13: | ||
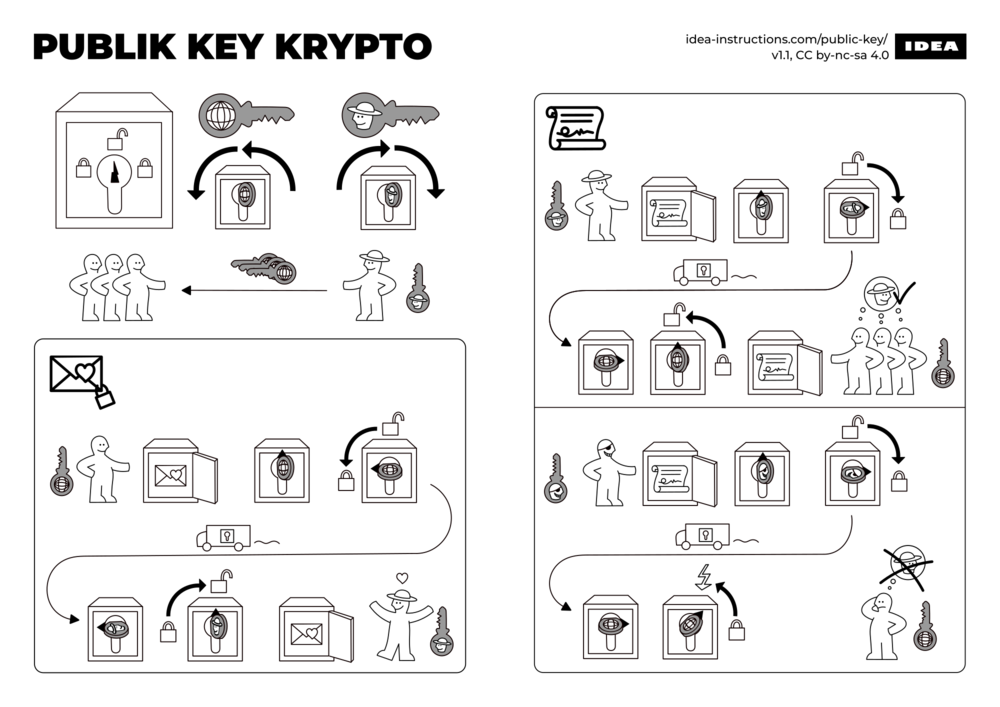
This diagram should help explain some of the principles. |
This diagram should help explain some of the principles. |
||
[[File:Public-key.png]] |
[[File:Public-key.png|1000px]] |
||
=How to use PGP= |
=How to use PGP= |
||
| Line 36: | Line 35: | ||
==Trust== |
==Trust== |
||
One of the big issues with any system for associating an identity with a person (e.g. a PGP key with a real person) is proving that link. How do you know someone is who they say they are. How do you know that someone's key is theirs |
One of the big issues with any system for associating an identity with a person (e.g. a PGP key with a real person) is proving that link. How do you know someone is who they say they are. How do you know that someone's key is theirs? |
||
All keys have a fingerprint which is easy enough to read out over the phone or check on a business card, etc. This is one way to check a key is genuine. You can then tell the key management software you trust the key |
All keys have a fingerprint, which is easy enough to read out over the phone or check on a business card, etc. This is one way to check a key is genuine. You can then tell the key management software that you trust that the key is genuine. |
||
It is also possible to say that you trust someone to sign other keys. For example, if you trust the Andrews & Arnold Ltd company key to sign other keys, then any of our staff keys will immediately appear to be valid when you download them from a key server because the key itself is digitally signed by the Andrews & Arnold Ltd company key. |
It is also possible to say that you trust someone to sign other keys. For example, if you trust the Andrews & Arnold Ltd company key to sign other keys, then any of our staff keys will immediately appear to be valid when you download them from a key server because the key itself is digitally signed by the Andrews & Arnold Ltd company key. |
||
Even without knowing someone is who they say they are PGP provides a |
Even without knowing someone is who they say they are, PGP provides a crucial factor for communications - consistency. If you have been exchanging signed emails with someone called Fred Bloggs for years, then that is in effect who they are from your point of view. If they send an email with the same key as always, it is the same person you communicated with last time. |
||
==Changing your key/passphrase== |
==Changing your key/passphrase== |
||
| Line 49: | Line 49: | ||
It is also possible to associate more names and email addresses with the same secret key, and revoke previous email address associations. This is handy if you use more than one email address, change email provider or even change your name as you can retain a consistent identity using the key. However, anyone counter signing your key only signs to say the association of name/email/etc with your key is valid and so would have to re-sign your key for other new people to trust it. Anyone who already trusts your key to represent you, would continue to do so. |
It is also possible to associate more names and email addresses with the same secret key, and revoke previous email address associations. This is handy if you use more than one email address, change email provider or even change your name as you can retain a consistent identity using the key. However, anyone counter signing your key only signs to say the association of name/email/etc with your key is valid and so would have to re-sign your key for other new people to trust it. Anyone who already trusts your key to represent you, would continue to do so. |
||
If you manage to expose your key, e.g. someone gets a copy and sees |
If you manage to expose your key, e.g. someone gets a copy and sees your passphrase, it is possible to revoke the key. This is a signed statement that you load on key servers saying that the key is no longer valid. There is no real way to ensure all possible senders and recipients get this though, so take care with your key. |
||
| ⚫ | You can set an expiry on a key. This helps if you think you may somehow expose the key to someone else. If you are confident in your own security principles, you could choose to have an non-expiring key. Expiring and changing keys can be inconvenient, but some people prefer to change keys every few years just to be sure no old key can possibly still be valid. |
||
| ⚫ | You can set an expiry on a key. This helps if you think you may somehow expose the key to someone else. If you are confident in your own security principles you could choose to have an non |
||
==Should you sign all emails?== |
==Should you sign all emails?== |
||
Latest revision as of 12:21, 13 August 2022
Introduction
PGP (Pretty Good Privacy) is a system that allows digital signatures and encryption. It is typically used for email. There is a wikipedia article on PGP which explains some of the history.
Basics
The basic principle of PGP is that you personally get yourself a key. This is conceptually much like a real key - it locks and unlocks things in effect. The thing is that the key is yours and yours alone.
There are a number of applications that let you use PGP, and one of the common ones is to use it for email. This then lets you digitally sign your emails using your key so that the recipient knows it is from you and has not been changed in any way. This also lets people encrypt email to you which only your key can unlock - i.e. nobody else can ever read the contents of the email.
This diagram should help explain some of the principles.
How to use PGP
We recommend Thunderbird as an email client. You can install a plug-in to Thunderbird called enigmail which allows you to handle PGP emails.
Making a key
The first stage when using PGP is to make your own key. This is stored on your computer but can be copied to other computers you use. The key will usually have your name and email associated with it. Enigmail takes you through these initial stages step by step. The secret key is protected by a pass phrase. This is a long password that you can easily remember but is long enough to be hard for someone else to guess. Never tell anyone your pass phrase or disclose your secret key. Signing emails
You can set Enigmail to sign all emails, or emails to certain people or only when you select it. Many people do not have tools to handle signed emails, so will see extra junk on your signed emails, but people usually manage to ignore this and read the content of the email anyway.
To sign an email needs your secret key and you are asked for your pass phrase when the email is sent. This proves the email is from you and not just someone using your computer or email address.
Encrypting emails
To encrypt an email to send to someone you need their key (not yours). Don't worry, you don't actually get their secret key which I said you must never disclose, you get what is called their public key. This is a key that lets you lock your email to them so that only their secret key and pass-phrase can open it. You can get public keys from key servers and Enigmail provides tools to get people's keys. You can also upload your public key to the key-server so people can get it to send encrypted emails to you. However, there is no immediate way to know someone's key is in fact theirs and not simply someone who made a key with the same name and email address (see Trust).
You can encrypt an email for several people and any of them can read it. However, once encrypted, nobody else can read the email (not even you). There is an option to always encrypt emails for yourself too so you can at least read your sent emails.
If you receive an encrypted email you will need to enter your pass-phrase. Only with your secret key and your pass-phrase can you read an email encrypted for you.
Trust
One of the big issues with any system for associating an identity with a person (e.g. a PGP key with a real person) is proving that link. How do you know someone is who they say they are. How do you know that someone's key is theirs?
All keys have a fingerprint, which is easy enough to read out over the phone or check on a business card, etc. This is one way to check a key is genuine. You can then tell the key management software that you trust that the key is genuine.
It is also possible to say that you trust someone to sign other keys. For example, if you trust the Andrews & Arnold Ltd company key to sign other keys, then any of our staff keys will immediately appear to be valid when you download them from a key server because the key itself is digitally signed by the Andrews & Arnold Ltd company key.
Even without knowing someone is who they say they are, PGP provides a crucial factor for communications - consistency. If you have been exchanging signed emails with someone called Fred Bloggs for years, then that is in effect who they are from your point of view. If they send an email with the same key as always, it is the same person you communicated with last time.
Changing your key/passphrase
It is worth bearing in mind that it is your secret key that is important. The passphrase protects the key. You can put the same key on more than one computer and have different passphrases if you like. Changing the passphrase does not mean you cannot read previously received encrypted emails, as long as they use the same underlying secret key.
It is also possible to associate more names and email addresses with the same secret key, and revoke previous email address associations. This is handy if you use more than one email address, change email provider or even change your name as you can retain a consistent identity using the key. However, anyone counter signing your key only signs to say the association of name/email/etc with your key is valid and so would have to re-sign your key for other new people to trust it. Anyone who already trusts your key to represent you, would continue to do so.
If you manage to expose your key, e.g. someone gets a copy and sees your passphrase, it is possible to revoke the key. This is a signed statement that you load on key servers saying that the key is no longer valid. There is no real way to ensure all possible senders and recipients get this though, so take care with your key.
You can set an expiry on a key. This helps if you think you may somehow expose the key to someone else. If you are confident in your own security principles, you could choose to have an non-expiring key. Expiring and changing keys can be inconvenient, but some people prefer to change keys every few years just to be sure no old key can possibly still be valid.
Should you sign all emails?
Do you sign all letters you send? The usual answer is yes, so why not sign all emails you send. If nothing else this helps establish that you are the same person that sent all the emails over a period of time. The only downside is that some people don't have the tools to check signatures and see extra junk on the email you sent. This can be particularly unpopular on mailing lists, so you may want to refrain from signing emails where the recipient finds it annoying - or possibly only sign emails to those that can cope with it.
Should you encrypt all emails where possible?
You can only encrypt an email to someone if you have their public key which generally means they can handle encrypted emails. If they can handle them, why not always encrypt them? Bear in mind some people have email on mobile phones, and other applications where maybe they cannot read the encrypted email so this may be less than ideal in some case.
There is however a good argument for encrypting as much as possible. It helps dilute the idea that encrypted emails means you have something to hide. After all, nobody says using opaque envelopes means you have something to hide, and people would not want all of their personal letters sent in clear envelopes. If encrypting email is routine then it makes invasion of privacy harder generally. Privacy is a basic human right and we should do everything we can to stop its erosion.