Stopping Open DNS - FireBrick 105: Difference between revisions
No edit summary |
No edit summary |
||
| Line 5: | Line 5: | ||
[[File:FireBrick-icons.png]] |
[[File:FireBrick-icons.png]] |
||
'''In a factory state the |
'''In a factory state the Filters on a FireBrick 105 will not allow DNS to the FireBrick from the WAN - the default state is to block incoming traffic, but to allow outgoing traffic. |
||
''' |
''' |
||
However, in some cases, customers disable the firewall by adding a rule that allows all traffic in. In this case, a new rule is needed to block DNS to the FireBrick. |
However, in some cases, customers disable the firewall by adding a rule that allows all traffic in. In this case, a new rule is needed to block DNS to the FireBrick. |
||
==Instructions== |
|||
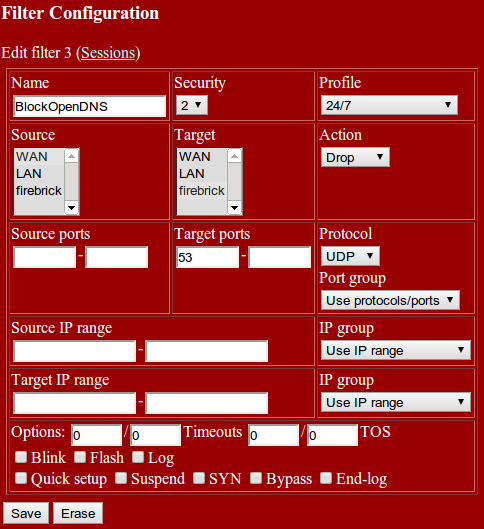
Create a Firewall filter to block port 53, from the WAN to the FireBrick, and make sure it's before any other rule that may allow this traffic in: |
Create a Firewall filter to block port 53, from the WAN to the FireBrick, and make sure it's before any other rule that may allow this traffic in: |
||
Revision as of 15:05, 18 June 2013
FireBrick 105:
In a factory state the Filters on a FireBrick 105 will not allow DNS to the FireBrick from the WAN - the default state is to block incoming traffic, but to allow outgoing traffic. However, in some cases, customers disable the firewall by adding a rule that allows all traffic in. In this case, a new rule is needed to block DNS to the FireBrick.
Instructions
Create a Firewall filter to block port 53, from the WAN to the FireBrick, and make sure it's before any other rule that may allow this traffic in:
Name: BlockOpenDNS Source: WAN Target: FireBrick (The name of your FireBrick) Action: Drop Target ports: 53 Protocol: UDP