Router - PFSense (beta 2.1): Difference between revisions
m (→Notes) |
mNo edit summary |
||
| (8 intermediate revisions by 3 users not shown) | |||
| Line 1: | Line 1: | ||
This is a short guide on getting a pfSense |
This is a short guide on getting a pfSense 2.0-[[IPv6]] and the 2.1 beta to connect to AAISP as a dual stack router and firewall. If you want more detail, pretty pictures and a full step by step guide, then post on the Discussion page and I'll consider it. |
||
Also, there is now a guide for more recent versions of pfSense (2.1.2+) that is also available here: [[Router - PFSense]] |
|||
= pfSense with IPv4 and IPv6 = |
= pfSense with IPv4 and IPv6 = |
||
I recently persuaded [http://www.pfsense.org/ pfSense] running on an ALIX based system with a Draytek Vigor 140 ADSL modem to connect up with IPv4 and IPv6 to AAISP. Here are some notes on how. That there are some minor faults with it but for the use case presented here it works fine and 2.1 is due for release fairly soon. They have a Redmine bug tracker that you can follow and the forums are excellent for support. The developers are on the ball. |
I recently persuaded [http://www.pfsense.org/ pfSense] running on an ALIX based system with a Draytek Vigor 140 [[ADSL Modem|ADSL modem]] to connect up with IPv4 and [[IPv6]] to AAISP. Here are some notes on how. That there are some minor faults with it but for the use case presented here it works fine and 2.1 is due for release fairly soon. They have a Redmine bug tracker that you can follow and the forums are excellent for support. The developers are on the ball. |
||
= Hardware = |
= Hardware = |
||
| Line 15: | Line 17: | ||
= Addressing = |
= Addressing = |
||
For IPv6, AAISP supply you with a /48 prefix from which you can create multiple /64 subnets for your use. There are over 65,000 /64 subnets in a /48 each with more addresses than you can eat! Click on the green "add /64" button on your control page to create them. |
For [[IPv6]], AAISP supply you with a /48 prefix from which you can create multiple /64 subnets for your use. There are over 65,000 /64 subnets in a /48 each with more addresses than you can eat! Click on the green "add /64" button on your control page to create them. |
||
For IPv4, note down the single /32 address and additional subnet range that you should have been assigned. The single address is the router's external address and the subnet is your LAN. |
For IPv4, note down the single /32 address and additional subnet range that you should have been assigned. The single address is the router's external address and the subnet is your LAN. |
||
| Line 26: | Line 28: | ||
Follow one of the many guides out there. It can be tricky to work out which interface is which, so plug one in, configure it at the initial console based interface setup stage, give it an IP address from your LAN range and set the mask. Then try and ping it after putting another address from the range temporarily on a PC or whatever. If it doesn't work then move the LAN cable into another NIC and see if that works. Once LAN is sorted, fire up a browser and point it at the LAN address and carry on the configuration from there. Username: admin, password: pfsense. I recommend you move the web GUI port to another port and enable SSL. There's a built in certificate generator so there is no excuse. |
Follow one of the many guides out there. It can be tricky to work out which interface is which, so plug one in, configure it at the initial console based interface setup stage, give it an IP address from your LAN range and set the mask. Then try and ping it after putting another address from the range temporarily on a PC or whatever. If it doesn't work then move the LAN cable into another NIC and see if that works. Once LAN is sorted, fire up a browser and point it at the LAN address and carry on the configuration from there. Username: admin, password: pfsense. I recommend you move the web GUI port to another port and enable SSL. There's a built in certificate generator so there is no excuse. |
||
Start with IPv4 and then move on to IPv6. |
Start with IPv4 and then move on to [[IPv6]]. |
||
The default firewall set up is no inbound access at all and just IPv4 out from the LAN subnet. |
The default firewall set up is no inbound access at all and just IPv4 out from the LAN subnet. |
||
| Line 44: | Line 46: | ||
=== IPv6 === |
=== IPv6 === |
||
* Set the IPv6 configuration type on your PPPoE interface to DHCPv6 |
* Set the [[IPv6 Configuration|IPv6 configuration]] type on your PPPoE interface to DHCPv6 |
||
* Set the IPv6 on LAN to <your /64 range>::1 (it doesn't have to be 1) and the mask to 64. |
* Set the [[IPv6]] on LAN to <your /64 range>::1 (it doesn't have to be 1) and the mask to 64. e.g. 2001:8b0:fc5c:6a01::1. |
||
* Services -> DHCPv6 Server/RA. Set Router Advertisements to Unmanaged |
* Services -> DHCPv6 Server/RA. Set Router Advertisements to Unmanaged |
||
Have a look at the addresses on your PC ("ip a"/"ifconfig"/"ipconfig /all") and you should find that you now have a global IPv6 address assigned. It will start with the /64 prefix from above. |
Have a look at the addresses on your PC ("ip a"/"ifconfig"/"ipconfig /all") and you should find that you now have a global [[IPv6]] address assigned. It will start with the /64 prefix from above. |
||
If you have additional interfaces then simply add another /64 on your AAISP control page and then set the IPv6 address to <another one of your /64s>::1. Then set RA to unmanaged as above for that interface |
If you have additional interfaces then simply add another /64 on your AAISP control page and then set the [[IPv6]] address to <another one of your /64s>::1. Then set RA to unmanaged as above for that interface |
||
Unmanaged really means use "radvd" |
Unmanaged really means use "radvd" i.e. auto addressing based on subnet and MAC address. There are several other options and these are described nicely on the page but unmanaged gets you up and running quickly. |
||
Add some IPv6 rules - |
Add some [[IPv6]] rules - e.g. on the LAN interface: "allow from LAN subnet to any". |
||
Test with something like "ping6 -n www.google.com" (adjust for OS) |
Test with something like "ping6 -n www.google.com" (adjust for OS) |
||
| Line 61: | Line 63: | ||
= Notes = |
= Notes = |
||
*Do not be tempted by the Widescreen package until it has been ported - it removes the web GUI IPv6 related stuff. |
*Do not be tempted by the Widescreen package until it has been ported - it removes the web GUI [[IPv6]] related stuff. |
||
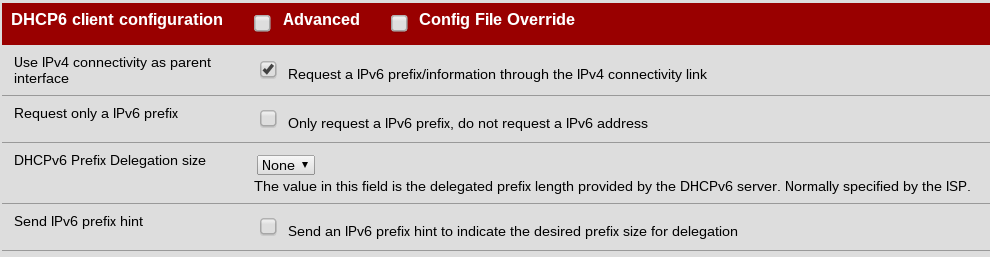
A customer noted that Setting 'Request a IPv6 prefix/information through the IPv4 connectivity link' helped him: |
A customer noted that Setting 'Request a [[IPv6]] prefix/information through the IPv4 connectivity link' helped him: |
||
[[File:Pfsensev6config.png]] |
[[File:Pfsensev6config.png]] |
||
This causes pfSense to change the interface in /var/etc/dhcpv6_wan.conf from em0 to pppoe0 (obviously dependent on hardware) - although the 'IPv4 connectivity link' description is a bit misleading . The following bug reports sent me in the right direction: |
This causes pfSense to change the interface in /var/etc/dhcpv6_wan.conf from em0 to pppoe0 (obviously dependent on hardware) - although the 'IPv4 connectivity link' description is a bit misleading . The following bug reports sent me in the right direction: |
||
[http://forum.pfsense.org/index.php?topic=65832.0] |
*[http://forum.pfsense.org/index.php?topic=65832.0 forum.pfsense.org/index.php?topic=65832.0] |
||
[https://redmine.pfsense.org/issues/3097] |
*[https://redmine.pfsense.org/issues/3097 redmine.pfsense.org/issues/3097] |
||
[[Category: |
[[Category:3rd Party Routers|PFSense]] |
||
Latest revision as of 09:21, 25 February 2015
This is a short guide on getting a pfSense 2.0-IPv6 and the 2.1 beta to connect to AAISP as a dual stack router and firewall. If you want more detail, pretty pictures and a full step by step guide, then post on the Discussion page and I'll consider it.
Also, there is now a guide for more recent versions of pfSense (2.1.2+) that is also available here: Router - PFSense
pfSense with IPv4 and IPv6
I recently persuaded pfSense running on an ALIX based system with a Draytek Vigor 140 ADSL modem to connect up with IPv4 and IPv6 to AAISP. Here are some notes on how. That there are some minor faults with it but for the use case presented here it works fine and 2.1 is due for release fairly soon. They have a Redmine bug tracker that you can follow and the forums are excellent for support. The developers are on the ball.
Hardware
The example ALIX system I have is a bit pricey but it comes with pfSense already installed and three 100Mb interfaces. You can get just the board and do it yourself quite easily for a lot less. Make sure you have some way to access the RS232 based console in some way in case it all goes wrong if you use this box.
A very good alternative is an old PC. Either put several network cards in it or get a switch such as a Netgear 108 and learn about 802.1Q VLANs to make one NIC into several.
You need at least two interfaces, one for LAN and one for WAN
Software
At the time of writing (20 May 2012) you need a development snapshot from the 2.1 series. Make sure it is post the date of this write up.
Addressing
For IPv6, AAISP supply you with a /48 prefix from which you can create multiple /64 subnets for your use. There are over 65,000 /64 subnets in a /48 each with more addresses than you can eat! Click on the green "add /64" button on your control page to create them.
For IPv4, note down the single /32 address and additional subnet range that you should have been assigned. The single address is the router's external address and the subnet is your LAN.
Configuration
Vigor
Plug the Vigor into a PC and point a browser at it. Check the output of "netstat -r"/"ipconfig /all"/"ip r" to find out its address (probably 192.168.2.1/24). There is no username and password by default. Now give it a new address and admin password. Make sure that it gets SHOWTIME for ADSL. It wont be able to login yet but at least you can verify the ADSL bit.
pfSense
Follow one of the many guides out there. It can be tricky to work out which interface is which, so plug one in, configure it at the initial console based interface setup stage, give it an IP address from your LAN range and set the mask. Then try and ping it after putting another address from the range temporarily on a PC or whatever. If it doesn't work then move the LAN cable into another NIC and see if that works. Once LAN is sorted, fire up a browser and point it at the LAN address and carry on the configuration from there. Username: admin, password: pfsense. I recommend you move the web GUI port to another port and enable SSL. There's a built in certificate generator so there is no excuse.
Start with IPv4 and then move on to IPv6.
The default firewall set up is no inbound access at all and just IPv4 out from the LAN subnet.
IPv4
Set a static IPv4 address on WAN that is in the same range as the Vigor. Create an outbound NAT rule from the LAN subnet to the WAN subnet. The Vigor has no routing table as such but pf can NAT you to it.
Create a PPPoE connection in Interfaces -> (assign) -> PPPs. Set your username and password.
Go to Interfaces -> (assign), add a new interface and assign the PPP to it. Call it something like AAISP.
If you prefer, you could rename your WAN to WANBASE and the PPPoE interface to WAN to avoid confusion when reading docs. However, if you use multiple ISPs then I suggest nameing the base interface to ISPBASE or ISPNIC and the PPPoE to ISP. It makes life a lot easier when you are managing it (my work one has six WANs on it!)
At this point you should be able to browse the internet and connect to the Vigor. The PPPoE interface should have the /32 address assigned to you by AAISP - check it in Status -> Interfaces.
Get some firewall rules set up (make sure that you set them to IPv4) and generally get the hang of the system.
IPv6
- Set the IPv6 configuration type on your PPPoE interface to DHCPv6
- Set the IPv6 on LAN to <your /64 range>::1 (it doesn't have to be 1) and the mask to 64. e.g. 2001:8b0:fc5c:6a01::1.
- Services -> DHCPv6 Server/RA. Set Router Advertisements to Unmanaged
Have a look at the addresses on your PC ("ip a"/"ifconfig"/"ipconfig /all") and you should find that you now have a global IPv6 address assigned. It will start with the /64 prefix from above.
If you have additional interfaces then simply add another /64 on your AAISP control page and then set the IPv6 address to <another one of your /64s>::1. Then set RA to unmanaged as above for that interface
Unmanaged really means use "radvd" i.e. auto addressing based on subnet and MAC address. There are several other options and these are described nicely on the page but unmanaged gets you up and running quickly.
Add some IPv6 rules - e.g. on the LAN interface: "allow from LAN subnet to any".
Test with something like "ping6 -n www.google.com" (adjust for OS)
Check http://test-ipv6.com/ for a full dual stack test.
Notes
- Do not be tempted by the Widescreen package until it has been ported - it removes the web GUI IPv6 related stuff.
A customer noted that Setting 'Request a IPv6 prefix/information through the IPv4 connectivity link' helped him:
This causes pfSense to change the interface in /var/etc/dhcpv6_wan.conf from em0 to pppoe0 (obviously dependent on hardware) - although the 'IPv4 connectivity link' description is a bit misleading . The following bug reports sent me in the right direction: