FireBrick Portmapping: Difference between revisions
mNo edit summary |
Fixup syntax |
||
| Line 11: | Line 11: | ||
[[File:Firebrick-portmap-ruleset.png|thumb|The Ruleset]] |
[[File:Firebrick-portmap-ruleset.png|thumb|The Ruleset]] |
||
<syntaxhighlight lang=xml> |
|||
<rule-set name="Port Mappings" |
|||
source-interface="pppoe" |
|||
source-interface="pppoe" |
|||
target-interface="self" |
|||
no-match-action="continue"> |
|||
</rule-set> |
|||
</syntaxhighlight> |
|||
And then add a rule for RDP to this rule-set: |
And then add a rule for RDP to this rule-set: |
||
<syntaxhighlight lang=xml> |
|||
<rule name="Map RDP to server1" |
|||
target-port="3389" |
|||
target-port="3389" |
|||
set-target-ip="192.168.1.101" |
|||
set-nat="true" |
|||
action="accept"/> |
|||
</syntaxhighlight> |
|||
You can add more requirements as needed, such as changing the port if needed, or adding source IPs so as to restrict access to known IPs. You can also use profiles to control access further. |
You can add more requirements as needed, such as changing the port if needed, or adding source IPs so as to restrict access to known IPs. You can also use profiles to control access further. |
||
If you have more port mappings then you can add more rule's as required, eg to add access to an internal web server you could map port 8080 to port 80 of the internal webserver: |
If you have more port mappings then you can add more rule's as required, eg to add access to an internal web server you could map port 8080 to port 80 of the internal webserver: |
||
[[File:Firebrick-portmap-rule.png|thumb|The rule]] |
[[File:Firebrick-portmap-rule.png|thumb|The rule]] |
||
<syntaxhighlight lang=xml> |
|||
<rule name="Map 8080 to web server2" |
|||
target-port="8080" |
|||
target-port="8080" |
|||
set-target-ip="192.168.1.102" |
|||
set-target-port="80" |
|||
set-nat="true" |
|||
action="accept"/> |
|||
</syntaxhighlight> |
|||
You can then test this rule using the built in Firewall test diagnostic. |
You can then test this rule using the built in Firewall test diagnostic. |
||
If you put in: |
If you put in: |
||
* |
* Source IP = anything you want |
||
*Target IP = The FireBrick's IP |
* Target IP = The FireBrick's IP |
||
*Protocol = 17 |
* Protocol = 17 |
||
*Target port = 3389 |
* Target port = 3389 |
||
Then you should see it match your rule and change the target IP etc: |
Then you should see it match your rule and change the target IP etc: |
||
Latest revision as of 00:10, 7 July 2021
FireBrick port mapping example
Mapping is done using Firewall rules.
The principle is that you describe the original traffic (source/target interface, IP, protocol, port etc) and then define a Rule with what you want to happen to that traffic - eg, set a new target IP, port and enable NAT.
Typically, your FireBrick will be the original target of the traffic, it will have a public IP on one of its PPP interfaces perhaps. If we take an example for RDP, then we can crate the rule-set as follows:
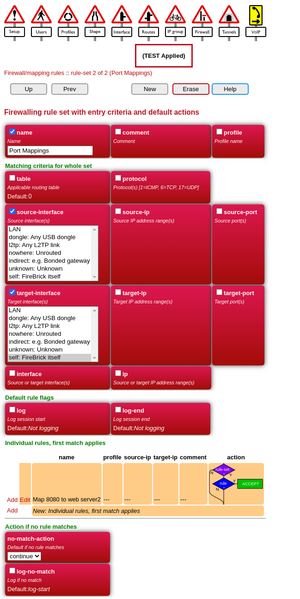
<rule-set name="Port Mappings"
source-interface="pppoe"
target-interface="self"
no-match-action="continue">
</rule-set>
And then add a rule for RDP to this rule-set:
<rule name="Map RDP to server1"
target-port="3389"
set-target-ip="192.168.1.101"
set-nat="true"
action="accept"/>
You can add more requirements as needed, such as changing the port if needed, or adding source IPs so as to restrict access to known IPs. You can also use profiles to control access further.
If you have more port mappings then you can add more rule's as required, eg to add access to an internal web server you could map port 8080 to port 80 of the internal webserver:
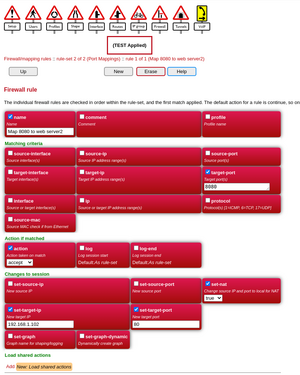
<rule name="Map 8080 to web server2"
target-port="8080"
set-target-ip="192.168.1.102"
set-target-port="80"
set-nat="true"
action="accept"/>
You can then test this rule using the built in Firewall test diagnostic.
If you put in:
- Source IP = anything you want
- Target IP = The FireBrick's IP
- Protocol = 17
- Target port = 3389
Then you should see it match your rule and change the target IP etc:
Checking rule-set 5 [Mapping] - Rule 3 [RDP to server1] matched, action is ACCEPT, no further rule-sets considered NAT set (true) Target IP set to 192.168.1.101