Stopping Open DNS - Billion: Difference between revisions
No edit summary |
mNo edit summary |
||
| (3 intermediate revisions by the same user not shown) | |||
| Line 5: | Line 5: | ||
This was tested on Firmware Version : 2.7.0.23(UE0.C2C)3.5.10.1 |
This was tested on Firmware Version : 2.7.0.23(UE0.C2C)3.5.10.1 |
||
[[File:Billion_dns_filter1.jpg]] |
[[File:Billion_dns_filter1.jpg|400px]] |
||
*Then re-test from the Control Pages: https://clueless.aa.net.uk/dnsresolvers.cgi |
|||
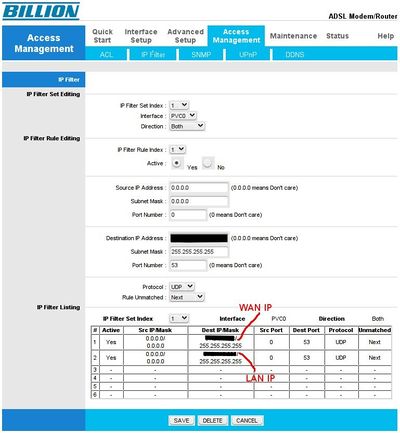
Please note that on these routers this does not prevent the router's internal resolver from doing the DNS lookup itself. This isn't usually a problem, but due to recent DNS amplification attacks sometimes lookups have continued after fixing the original problem. To prevent this add a rule blocking DNS *from* the router's WAN IP *to* port 53. This will prevent usage of the router as the LAN's DNS resolver. |
Please note that on these routers this does not prevent the router's internal resolver from doing the DNS lookup itself. This isn't usually a problem, but due to recent DNS amplification attacks sometimes lookups have continued after fixing the original problem. To prevent this add a rule blocking DNS *from* the router's WAN IP *to* port 53. This will prevent usage of the router as the LAN's DNS resolver. |
||
[[Category:Open DNS Resolvers]] |
[[Category:Open DNS Resolvers]] |
||
[[Category: |
[[Category:3rd Party Routers]] |
||
Latest revision as of 09:22, 25 February 2015
Billion
Billion routers appear to have a built-in DNS resolver, and answer queries on the WAN interface by default, so is vulnerable to taking part in DDoS attacks by replying to spoofed dns queries. Screenshot below shows how to block this in filters.
This was tested on Firmware Version : 2.7.0.23(UE0.C2C)3.5.10.1
- Then re-test from the Control Pages: https://clueless.aa.net.uk/dnsresolvers.cgi
Please note that on these routers this does not prevent the router's internal resolver from doing the DNS lookup itself. This isn't usually a problem, but due to recent DNS amplification attacks sometimes lookups have continued after fixing the original problem. To prevent this add a rule blocking DNS *from* the router's WAN IP *to* port 53. This will prevent usage of the router as the LAN's DNS resolver.