FireBrick Road Warrior Windows 7: Difference between revisions
mNo edit summary |
m clean up, typos fixed: eg → e.g. (2) |
||
| (20 intermediate revisions by one other user not shown) | |||
| Line 1: | Line 1: | ||
<indicator name="RoadW">[[File:Menu-Road-Warrior.svg|link=:Category: |
<indicator name="RoadW">[[File:Menu-Road-Warrior.svg|link=:Category:FireBrick IPsec Road Warrior|30px|Back up to the FireBrick Road Warrior Category Page]]</indicator> |
||
== Windows setup == |
== Windows setup == |
||
| Line 7: | Line 7: | ||
The CA certificate needs to be installed on the Windows machine using an account with administrator privileges. |
The CA certificate needs to be installed on the Windows machine using an account with administrator privileges. |
||
| ⚫ | |||
===Download the Certificate=== |
|||
use a browser to visit your FireBrick certificate management page, and click on the Download DER link corresponding |
|||
to the CA certificate. Save it in a suitable location on the Windows machine. Do not attempt to execute it or |
|||
The CA certificate needs to be installed on the Windows machine using an account with administrator privileges. |
|||
| ⚫ | |||
recognize PEM format. The file will be given the <tt>.crt</tt> extension. |
|||
| ⚫ | |||
#Use a browser (ed 'Edge') to visit your FireBrick |
|||
##Go to: Config - Certificates to reach the certificate management page |
|||
##Click on the Download DER link corresponding to the CA certificate. |
|||
| ⚫ | |||
===Start the Windows Certificate Manager=== |
===Start the Windows Certificate Manager=== |
||
The Windows certificate manager should now be started up as follows: |
The Windows certificate manager should now be started up as follows: |
||
# Using a command window, or the Start|Run box, execute the command <tt>mmc</tt> (and answer Yes when asked if you want to allow changes). |
# Using a command window, or the '''Start|Run''' box, execute the command <tt>'''mmc'''</tt> (and answer Yes when asked if you want to allow changes). |
||
# Select Add/Remove Snap-in from the File menu, choose the Certificates snap-in and add it to selected snap-ins. |
# Select '''Add/Remove Snap-in''' from the File menu, choose the '''Certificates''' snap-in and add it to selected snap-ins. |
||
# A dialog will ask if you want to manage certificates for the user account, a service account or computer account. You must select <tt>Computer Account</tt> here in order to manage the system certificates. If you do not select this, or you start up the certificate manager in some other way ( |
# A dialog will ask if you want to manage certificates for the user account, a service account or computer account. You must select <tt>'''Computer Account'''</tt> here in order to manage the system certificates. If you do not select this, or you start up the certificate manager in some other way (e.g. using <tt>certmgr.msc</tt>, you will not be able to install the certificate system-wide, and the Windows IPsec subsystem will not find it. Click '''Next'''. |
||
# Another dialog will ask which computer to manage. Choose <tt>Local computer</tt>. |
# Another dialog will ask which computer to manage. Choose <tt>'''Local computer'''</tt>. Click '''Finish''' |
||
# Finally click on <tt>OK</tt> to start the certificate manger snap-in. |
# Finally click on <tt>'''OK'''</tt> to start the certificate manger snap-in. |
||
===Install the CA certificate=== |
===Install the CA certificate=== |
||
To install the certificate: |
To install the certificate: |
||
# Double-click on <tt>Certificates (Local Computer)</tt> in the left pane, to open the certificate store names |
# Double-click on <tt>'''Certificates (Local Computer)'''</tt> in the left pane, to open the certificate store names |
||
#then right-click on <tt>'''Trusted Root Certification Authorities'''</tt> in the centre pane. |
|||
# Select <tt>All Tasks</tt> and then <tt>Import...</tt> |
# Select <tt>'''All Tasks'''</tt> and then <tt>'''Import...'''</tt> |
||
# Click <tt>Next</tt> and browse to where you saved the CA .crt file. |
|||
# Click <tt>Next</tt> and |
# Click <tt>'''Next'''</tt> and '''browse''' to where you saved the CA .crt file. (Usually in your Downloads folder) |
||
#Select the .crt file and click '''Open''' |
|||
| ⚫ | |||
# Click <tt>'''Next'''</tt> and check that the certificate will be placed in the trusted root store. |
|||
| ⚫ | |||
#A window will pop up saying 'The Import was successful. Click '''OK''' |
|||
#You can now close the mmc console, File - Exit. No need to save. |
|||
There - wasn't that easy! Thank you Microsoft. |
There - wasn't that easy! Thank you Microsoft. |
||
| Line 35: | Line 44: | ||
Now you need to set up the IPsec network connection details. |
Now you need to set up the IPsec network connection details. |
||
# Go to Control Panel and |
# Go to Start - '''Control Panel''' then Network and Internet, then 'View network status and tasks then <tt>'''Set up a new connection or network'''</tt>. |
||
# Select <tt>Connect to a Network</tt> and choose <tt>Connect to a Workplace</tt>. |
# Select <tt>Connect to a Network</tt> and choose <tt>'''Connect to a Workplace'''</tt>. |
||
# Click <tt>Next</tt>, select <tt>No, create a new connecton</tt>, <tt>Next</tt> |
# Click <tt>Next</tt>, select <tt>No, create a new connecton</tt>, <tt>Next</tt> |
||
# Choose <tt>Use my Internet connection</tt> |
# Choose <tt>Use my Internet connection (VPN)</tt> |
||
# Insert the server name ( |
# Insert the server name (e.g. <tt>server.example.com</tt>), and choose whatever you like to name the connection (Destination name). (the Server name needs to match the name in the generated certificate, this is usually a hostname rather than an IP address) |
||
# Select <tt>Don't connect now; ...</tt> |
# Select <tt>'''Don't connect now; ...'''</tt> |
||
# You don't need to enter User name and password as it will ask again later |
# You don't need to enter User name and password as it will ask again later |
||
# Click on <tt>Create</tt> and then <tt>Close</tt> (Don't connect yet!) |
# Click on <tt>'''Create'''</tt> and then <tt>'''Close'''</tt> (Don't connect yet!) |
||
# Back at the Network and Sharing Center dialog, select <tt>Connect to a network</tt> |
# Back at the Network and Sharing Center dialog, select <tt>'''Connect to a network'''</tt> |
||
# Right-click the connection you have just created in the pop-up box and select <tt>Properties</tt> |
# Right-click the connection you have just created in the pop-up box and select <tt>Properties</tt> |
||
# Select the <tt>Security</tt> tab, and change the Type of VPN to IKEv2. |
# Select the <tt>Security</tt> tab, and change the Type of VPN to IKEv2. |
||
| Line 56: | Line 65: | ||
=Help= |
|||
[[Category:FireBrick_IPsec_Road_Warrior]] |
|||
==Error 13801: IKE authentication credentials are unacceptable== |
|||
[[File:Win7-IPsec-error-ike2auth.PNG|framed|none|Error 13801]] |
|||
#Check that the hostname as set in the VPN settings matches the server certificate name, or: |
|||
#Double check that you selected 'Computer Account' in the steps above for the installing the certificate in the Certificate Manager |
|||
[[Category:FireBrick IPsec Road Warrior|Windows]] |
|||
Latest revision as of 00:00, 15 March 2017
Windows setup
The following instructions were tested on a Windows 7 system. Setup on other versions of Windows will be similar, but the dialogs and messages seen may not be exactly as shown here.
The CA certificate needs to be installed on the Windows machine using an account with administrator privileges.
Download the Certificate
The CA certificate needs to be installed on the Windows machine using an account with administrator privileges.
First, download the CA certificate in DER format to the Windows machine. The easiest way to do this is to@
- Use a browser (ed 'Edge') to visit your FireBrick
- Go to: Config - Certificates to reach the certificate management page
- Click on the Download DER link corresponding to the CA certificate.
- Save it in a suitable location on the Windows machine. Note that you must download the certificate in DER format - windows machines do not recognize PEM format. The file will be given the .crt extension.
Start the Windows Certificate Manager
The Windows certificate manager should now be started up as follows:
- Using a command window, or the Start|Run box, execute the command mmc (and answer Yes when asked if you want to allow changes).
- Select Add/Remove Snap-in from the File menu, choose the Certificates snap-in and add it to selected snap-ins.
- A dialog will ask if you want to manage certificates for the user account, a service account or computer account. You must select Computer Account here in order to manage the system certificates. If you do not select this, or you start up the certificate manager in some other way (e.g. using certmgr.msc, you will not be able to install the certificate system-wide, and the Windows IPsec subsystem will not find it. Click Next.
- Another dialog will ask which computer to manage. Choose Local computer. Click Finish
- Finally click on OK to start the certificate manger snap-in.
Install the CA certificate
To install the certificate:
- Double-click on Certificates (Local Computer) in the left pane, to open the certificate store names
- then right-click on Trusted Root Certification Authorities in the centre pane.
- Select All Tasks and then Import...
- Click Next and browse to where you saved the CA .crt file. (Usually in your Downloads folder)
- Select the .crt file and click Open
- Click Next and check that the certificate will be placed in the trusted root store.
- Click Next again, and then Finish.
- A window will pop up saying 'The Import was successful. Click OK
- You can now close the mmc console, File - Exit. No need to save.
There - wasn't that easy! Thank you Microsoft.
Set up the VPN Network Connection
Now you need to set up the IPsec network connection details.
- Go to Start - Control Panel then Network and Internet, then 'View network status and tasks then Set up a new connection or network.
- Select Connect to a Network and choose Connect to a Workplace.
- Click Next, select No, create a new connecton, Next
- Choose Use my Internet connection (VPN)
- Insert the server name (e.g. server.example.com), and choose whatever you like to name the connection (Destination name). (the Server name needs to match the name in the generated certificate, this is usually a hostname rather than an IP address)
- Select Don't connect now; ...
- You don't need to enter User name and password as it will ask again later
- Click on Create and then Close (Don't connect yet!)
- Back at the Network and Sharing Center dialog, select Connect to a network
- Right-click the connection you have just created in the pop-up box and select Properties
- Select the Security tab, and change the Type of VPN to IKEv2.
- EAP-MSCHAPv2 should already be selected.
- Click OK
You should now be ready to connect - select Connect to a network again, click on the connection and choose Connect. If not already saved, you'll use the username and password as set up in the EAP Identity on the FireBrick (in this example, we had set up a user of fred with a password)
You probably want to change the type of network to Work Network after the connection establishes.
Help
Error 13801: IKE authentication credentials are unacceptable
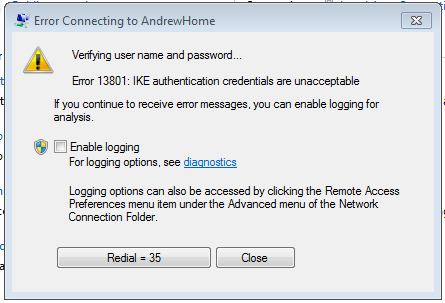
- Check that the hostname as set in the VPN settings matches the server certificate name, or:
- Double check that you selected 'Computer Account' in the steps above for the installing the certificate in the Certificate Manager