Fortigate IPv6: Difference between revisions
m tidy up slightly lol |
mNo edit summary |
||
| (6 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
also this blogpost (completely unrelated to A&A) may be useful: https://blah.cloud/networks/enabling-ipv6-dhcpv6-pd-pppoe-fortigate/ |
|||
=Version 7.2= |
|||
These details were updated late 2022 for Version 7.2 from a customer (thank you!) |
|||
[[File:Fortigate 7.2 Delegated IPv6 Diagram.jpg|thumb|center]] |
|||
Example set up to provide 3 ::/64 networks behind customer Fortigate using delegated IP from AA DHCPv6 server. For OS version 7.2 |
|||
Note with 7.2 it is possible to configure PPPoE on the wan interface directly and this works for IPv4 but not for IPv6. If the interface is PPPoE and ipV6 addresssing is set for DHCP for IPv6 no address is obtained So a PPoe subinterface still needs to used. |
|||
Also with 7.2 the "set ip6-delegated-prefix-iaid x" command must be used otherwise the PPPoE interface cannot be assigned as the upstream interface. |
|||
See https://community.fortinet.com/t5/Fortinet-Forum/Error-when-addin-IPv6-with-deligation-to-LAN-interface/m-p/199091 |
|||
and |
|||
https://blah.cloud/networks/enabling-ipv6-dhcpv6-pd-pppoe-fortigate/ |
|||
for more details as to what each command does. |
|||
Example configurations below note the three IPv6 subnets need to be replaced with ones assigned from AA control pages: |
|||
I've also assigned .1 as the firewall address but this is strictly not required |
|||
<syntaxhighlight lang=bash> |
|||
config system interface |
|||
edit "wan" |
|||
set type physical |
|||
set role wan |
|||
config ipv6 |
|||
end |
|||
set dns-server-override disable |
|||
next |
|||
edit "lan1" |
|||
set ip 192.168.1.1 255.255.255.0 |
|||
set type physical |
|||
set device-identification enable |
|||
set role lan |
|||
config ipv6 |
|||
set ip6-mode delegated |
|||
set ip6-allowaccess ping https ssh snmp http fgfm fabric |
|||
set ip6-send-adv enable |
|||
set ip6-manage-flag enable |
|||
set ip6-other-flag enable |
|||
set ip6-upstream-interface "PPPOE1" |
|||
set ip6-delegated-prefix-iaid 1 |
|||
set ip6-subnet ::1/64 |
|||
end |
|||
next |
|||
edit "lan2" |
|||
set ip 192.168.2.1 255.255.255.0 |
|||
set type physical |
|||
set device-identification enable |
|||
set role lan |
|||
config ipv6 |
|||
set ip6-mode delegated |
|||
set ip6-allowaccess ping https ssh snmp http fgfm fabric |
|||
set ip6-send-adv enable |
|||
set ip6-manage-flag enable |
|||
set ip6-other-flag enable |
|||
set ip6-upstream-interface "PPPOE1" |
|||
set ip6-delegated-prefix-iaid 2 |
|||
set ip6-subnet ::1/64 |
|||
end |
|||
next |
|||
edit "lan3" |
|||
set ip 192.168.3.1 255.255.255.0 |
|||
set type physical |
|||
set device-identification enable |
|||
set role lan |
|||
config ipv6 |
|||
set ip6-mode delegated |
|||
set ip6-allowaccess ping https ssh snmp http fgfm fabric |
|||
set ip6-send-adv enable |
|||
set ip6-manage-flag enable |
|||
set ip6-other-flag enable |
|||
set ip6-upstream-interface "PPPOE1" |
|||
set ip6-delegated-prefix-iaid 3 |
|||
set ip6-subnet ::1/64 |
|||
end |
|||
next |
|||
edit "PPPOE1" |
|||
set mode pppoe |
|||
set allowaccess ping |
|||
set type tunnel |
|||
set role wan |
|||
config ipv6 |
|||
set ip6-mode dhcp |
|||
set ip6-allowaccess ping |
|||
set dhcp6-prefix-delegation enable |
|||
config dhcp6-iapd-list |
|||
edit 1 |
|||
set prefix-hint 2001:8b0:xxxx:13fa9::/64 |
|||
next |
|||
edit 2 |
|||
set prefix-hint 2001:8b0:xxxx:13fb0::/64 |
|||
next |
|||
edit 3 |
|||
set prefix-hint 2001:8b0:xxxx:13fb1::/64 |
|||
next |
|||
end |
|||
end |
|||
set interface "wan" |
|||
next |
|||
config system dhcp6 server |
|||
edit 1 |
|||
set dns-service delegated |
|||
set interface "lan1" |
|||
set upstream-interface "PPPOE1" |
|||
set delegated-prefix-iaid 1 |
|||
set ip-mode delegated |
|||
next |
|||
edit 2 |
|||
set dns-service delegated |
|||
set interface "lan2" |
|||
set upstream-interface "PPPOE1" |
|||
set delegated-prefix-iaid 2 |
|||
set ip-mode delegated |
|||
next |
|||
edit 3 |
|||
set dns-service delegated |
|||
set interface "lan3" |
|||
set upstream-interface "PPPOE1" |
|||
set delegated-prefix-iaid 3 |
|||
set ip-mode delegated |
|||
next |
|||
end |
|||
</syntaxhighlight> |
|||
=(Older) Version 5.6= |
|||
From a customer: |
From a customer: |
||
Fortinet Fortigate Native IPv6 support on A&A's Network. |
Fortinet Fortigate Native IPv6 support on A&A's Network. |
||
| Line 6: | Line 135: | ||
Fortinet's Unified Threat Management (UTM) solutions are well regarded and provide indepdentedly reviewed and tested levels of protection against numerous threats. |
Fortinet's Unified Threat Management (UTM) solutions are well regarded and provide indepdentedly reviewed and tested levels of protection against numerous threats. |
||
In addition to fully stateful firewalls (typical in most consumer products) Fortigate and FortiWifi products support:- |
In addition to fully stateful firewalls (typical in most consumer products) Fortigate and FortiWifi products support:- |
||
* Full control of incoming and outgoing traffic flow ( |
* Full control of incoming and outgoing traffic flow (i.e. nothing can leave or enter the protected network unless explicitly permitted). |
||
* Anti-virus protection which can be applied to any firewall flow (removing viruses before traffic hits the end device). |
* Anti-virus protection which can be applied to any firewall flow (removing viruses before traffic hits the end device). |
||
* Botnet/ Command & Control server mitigation (preventing outgoing and incoming connections from known Botnet/ Command & Control servers). |
* Botnet/ Command & Control server mitigation (preventing outgoing and incoming connections from known Botnet/ Command & Control servers). |
||
* Web Filtering (which allows categories of sites to be allows or blocked. |
* Web Filtering (which allows categories of sites to be allows or blocked. e.g. media streaming sites can be blocked to prevent excess bandwidth usage). |
||
* Application control (allowing specific applications to be allowed or blocked. |
* Application control (allowing specific applications to be allowed or blocked. e.g. BitTorrents can be blocked to prevent downloads of potentially copyright information) |
||
* Dynamic updating of services to protect against new threats. |
* Dynamic updating of services to protect against new threats. |
||
* Support of entrprise features such as VLAN, QoS, Additional Wireless Access Points and advanced routing configurations. |
* Support of entrprise features such as VLAN, QoS, Additional Wireless Access Points and advanced routing configurations. |
||
| Line 25: | Line 154: | ||
To support this configuration on Fortigate/ Fortinet products requires the 5.6 release which became availabe in early April 2017. |
To support this configuration on Fortigate/ Fortinet products requires the 5.6 release which became availabe in early April 2017. |
||
This release supports "multiple PPPoE connections on a single interface (Feature 363958)" which allows the A&A native IPv6 config (IA and PD) to be |
This release supports "multiple PPPoE connections on a single interface (Feature 363958)" which allows the A&A native IPv6 config (IA and PD) to be successfully configured. |
||
Upgrade to this 5.6 release (or later if available) before attepmting to setup native IPv6 on your Fortigate. |
Upgrade to this 5.6 release (or later if available) before attepmting to setup native IPv6 on your Fortigate. |
||
Ideally, the setup is probably most easily setup on a default Fortigate/ FortiWifi configuration. |
Ideally, the setup is probably most easily setup on a default Fortigate/ FortiWifi configuration. |
||
| Line 32: | Line 161: | ||
In an existing configuration all policies need to be redirected to the new virtual interface once it has been configurated. For a new configuration new firewall polices are directed towards the virtual interface. |
In an existing configuration all policies need to be redirected to the new virtual interface once it has been configurated. For a new configuration new firewall polices are directed towards the virtual interface. |
||
Lastly, for IPv6 a default static route needs to be set toward the virtual interface. |
Lastly, for IPv6 a default static route needs to be set toward the virtual interface. |
||
I've not |
I've not covered the LAN side of the configuration. This configuration depends on your requirements- both stateless configurations (no DHCPv6 server with the client configuring it's IP address based on IPv6 prefix advertisements) and stateful (based on a DHCPv6 server are possible. |
||
== Configuration Details == |
== Configuration Details == |
||
Latest revision as of 13:14, 24 February 2023
also this blogpost (completely unrelated to A&A) may be useful: https://blah.cloud/networks/enabling-ipv6-dhcpv6-pd-pppoe-fortigate/
Version 7.2
These details were updated late 2022 for Version 7.2 from a customer (thank you!)
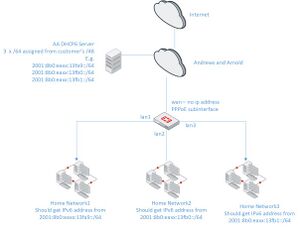
Example set up to provide 3 ::/64 networks behind customer Fortigate using delegated IP from AA DHCPv6 server. For OS version 7.2
Note with 7.2 it is possible to configure PPPoE on the wan interface directly and this works for IPv4 but not for IPv6. If the interface is PPPoE and ipV6 addresssing is set for DHCP for IPv6 no address is obtained So a PPoe subinterface still needs to used.
Also with 7.2 the "set ip6-delegated-prefix-iaid x" command must be used otherwise the PPPoE interface cannot be assigned as the upstream interface.
See https://community.fortinet.com/t5/Fortinet-Forum/Error-when-addin-IPv6-with-deligation-to-LAN-interface/m-p/199091 and https://blah.cloud/networks/enabling-ipv6-dhcpv6-pd-pppoe-fortigate/ for more details as to what each command does.
Example configurations below note the three IPv6 subnets need to be replaced with ones assigned from AA control pages: I've also assigned .1 as the firewall address but this is strictly not required
config system interface
edit "wan"
set type physical
set role wan
config ipv6
end
set dns-server-override disable
next
edit "lan1"
set ip 192.168.1.1 255.255.255.0
set type physical
set device-identification enable
set role lan
config ipv6
set ip6-mode delegated
set ip6-allowaccess ping https ssh snmp http fgfm fabric
set ip6-send-adv enable
set ip6-manage-flag enable
set ip6-other-flag enable
set ip6-upstream-interface "PPPOE1"
set ip6-delegated-prefix-iaid 1
set ip6-subnet ::1/64
end
next
edit "lan2"
set ip 192.168.2.1 255.255.255.0
set type physical
set device-identification enable
set role lan
config ipv6
set ip6-mode delegated
set ip6-allowaccess ping https ssh snmp http fgfm fabric
set ip6-send-adv enable
set ip6-manage-flag enable
set ip6-other-flag enable
set ip6-upstream-interface "PPPOE1"
set ip6-delegated-prefix-iaid 2
set ip6-subnet ::1/64
end
next
edit "lan3"
set ip 192.168.3.1 255.255.255.0
set type physical
set device-identification enable
set role lan
config ipv6
set ip6-mode delegated
set ip6-allowaccess ping https ssh snmp http fgfm fabric
set ip6-send-adv enable
set ip6-manage-flag enable
set ip6-other-flag enable
set ip6-upstream-interface "PPPOE1"
set ip6-delegated-prefix-iaid 3
set ip6-subnet ::1/64
end
next
edit "PPPOE1"
set mode pppoe
set allowaccess ping
set type tunnel
set role wan
config ipv6
set ip6-mode dhcp
set ip6-allowaccess ping
set dhcp6-prefix-delegation enable
config dhcp6-iapd-list
edit 1
set prefix-hint 2001:8b0:xxxx:13fa9::/64
next
edit 2
set prefix-hint 2001:8b0:xxxx:13fb0::/64
next
edit 3
set prefix-hint 2001:8b0:xxxx:13fb1::/64
next
end
end
set interface "wan"
next
config system dhcp6 server
edit 1
set dns-service delegated
set interface "lan1"
set upstream-interface "PPPOE1"
set delegated-prefix-iaid 1
set ip-mode delegated
next
edit 2
set dns-service delegated
set interface "lan2"
set upstream-interface "PPPOE1"
set delegated-prefix-iaid 2
set ip-mode delegated
next
edit 3
set dns-service delegated
set interface "lan3"
set upstream-interface "PPPOE1"
set delegated-prefix-iaid 3
set ip-mode delegated
next
end
(Older) Version 5.6
From a customer: Fortinet Fortigate Native IPv6 support on A&A's Network.
Introduction
The Fortinet range of Fortinet/ FortiWifi products are high end security products which are targeted towards corporate security solutions. Fortinet's Unified Threat Management (UTM) solutions are well regarded and provide indepdentedly reviewed and tested levels of protection against numerous threats. In addition to fully stateful firewalls (typical in most consumer products) Fortigate and FortiWifi products support:-
- Full control of incoming and outgoing traffic flow (i.e. nothing can leave or enter the protected network unless explicitly permitted).
- Anti-virus protection which can be applied to any firewall flow (removing viruses before traffic hits the end device).
- Botnet/ Command & Control server mitigation (preventing outgoing and incoming connections from known Botnet/ Command & Control servers).
- Web Filtering (which allows categories of sites to be allows or blocked. e.g. media streaming sites can be blocked to prevent excess bandwidth usage).
- Application control (allowing specific applications to be allowed or blocked. e.g. BitTorrents can be blocked to prevent downloads of potentially copyright information)
- Dynamic updating of services to protect against new threats.
- Support of entrprise features such as VLAN, QoS, Additional Wireless Access Points and advanced routing configurations.
While these features can be complex to setup they offer excellent levels of granularity, security and filering which make them useful in a larger or more advanced network. Products to support a small business or larger home network would generally be found in the 30-90 series of devices. Further information on Fortinet products can be found at https://www.fortinet.com/products/firewalls/firewall/fortigate-entry-level.html .
Fortigate/ FortiWifi Pre-requisities for IPv6 on A&A ISP
Native IPv6 on A&A's network requires:-
- WAN Interface Assignment based IA.
- Delegation of a block of IPv6 addresses based on DHCP-PD
This is described on the A&A website here https://support.aa.net.uk/Category:IPv6
To support this configuration on Fortigate/ Fortinet products requires the 5.6 release which became availabe in early April 2017. This release supports "multiple PPPoE connections on a single interface (Feature 363958)" which allows the A&A native IPv6 config (IA and PD) to be successfully configured. Upgrade to this 5.6 release (or later if available) before attepmting to setup native IPv6 on your Fortigate. Ideally, the setup is probably most easily setup on a default Fortigate/ FortiWifi configuration. Once the native IPv6 interface is setup a new virtual interface will be created which supports the native IPv6 connection as well as the IPv4 connection. On an existing configuration the IPv4 PPPoE configuration on the physical interface will need to be removed to avoid two entries in the IPv4 routing table. In an existing configuration all policies need to be redirected to the new virtual interface once it has been configurated. For a new configuration new firewall polices are directed towards the virtual interface. Lastly, for IPv6 a default static route needs to be set toward the virtual interface. I've not covered the LAN side of the configuration. This configuration depends on your requirements- both stateless configurations (no DHCPv6 server with the client configuring it's IP address based on IPv6 prefix advertisements) and stateful (based on a DHCPv6 server are possible.
Configuration Details
The first two steps need to be completed via CLI. You will need to be able to SSH into your Fortigate/ FortiWifi using Putty or a similar product.
Setup of the virtual WAN port via IA:-
config system pppoe-interface edit pppoe1 set ipv6 enable set device port4
Note that "pppoe1" will be the name of the virtual interface and "port4" will be your WAN port which has the virtual interface associated with it.
Setup of the Prefix Delegation:-
config system interface edit pppoe1 config ipv6 set ip6-mode dhcp set dhcp6-prefix-delegation enable end next end
This will allow the prefix (/64 is standard for A&A) to be assigned to the virtual interface.
Static Route
A static route can be set via the Web GUI or via CLI. It is set as follows:-
::/0 (ie all IPv6 addresses) pppoe1 (the destination virtual port created in steps 1 &2).