FireBrick Bonding more than 3 lines: Difference between revisions
| (19 intermediate revisions by 5 users not shown) | |||
| Line 1: | Line 1: | ||
[[File: |
<indicator name="Front">[[File:Menu-bonding.svg|link=:Category:Bonding|30px|Back up to the Bonding Page]]</indicator> |
||
=Overview= |
=Overview= |
||
The FireBrick 2500/2700 have 4 ethernet ports, the 2900 has 4 plus an SFP which can be used with a Copper of fibre SFP to give an additional port. Typically one port will be for the LAN connection (for example - to the main office switch), and the rest for connections to the ADSL/FTTC modems. |
|||
As there are 4 ports are we restricted to only bonding up to 3 ADSL/FTTC lines? No. |
|||
| ⚫ | |||
| ⚫ | |||
<pre> |
<pre> |
||
ADSL MODEM 1 -- |
ADSL MODEM 1 -- |
||
| Line 15: | Line 19: | ||
=VLAN Switch Config= |
=VLAN Switch Config= |
||
Instructions on using a ZyXEL GS1900-8 switch: [[ZyXEL GS1900-8]] |
|||
| ⚫ | |||
| ⚫ | |||
| ⚫ | |||
| ⚫ | |||
| ⚫ | |||
| ⚫ | |||
The FireBrick will have a single WAN port, which will plug in to the HP Switch. The ADSL modems will plug in to the HP Switch too. |
|||
The FireBrick will have a single WAN port, which will plug in to the HP Switch. The ADSL/FTTC modems will plug in to the HP Switch too. |
|||
This will then, with VLANs, enable the FireBrick to use up to 7 ADSL/FTTC modems. |
|||
*Default IP is "192.168.2.10" |
|||
*Default |
*Default username: admin |
||
*Default password |
*Default password: 1234 |
||
==Save Config== |
==Save Config== |
||
To make things a little easier, here is a saved config: [[File:FBVLANconfig1810G.bin.zip]]. It is the default config (default IP and password), but with VLANs as follows: |
To make things a little easier, here is a saved config: [[File:FBVLANconfig1810G.bin.zip]]. It is the default config (default IP and password), but with VLANs as follows: |
||
*Port 1 - VLAN 101, for ADSL line 1 |
*Port 1 - VLAN 101, for ADSL line 1 |
||
*Port 2 - VLAN |
*Port 2 - VLAN 102, for ADSL line 2 |
||
*Port 3 - VLAN |
*Port 3 - VLAN 103, for ADSL line 3 |
||
*Port 4 - VLAN |
*Port 4 - VLAN 104, for ADSL line 4 |
||
* |
*Port 8 is for the FireBrick |
||
The config was from HP ProCurve 1810G - 8 GE, P.1.17, eCos-2.0, Software Version, P.1.17 |
The config was from HP ProCurve 1810G - 8 GE, P.1.17, eCos-2.0, Software Version, P.1.17 |
||
| Line 41: | Line 46: | ||
==Basic Settings== |
==Basic Settings== |
||
*Set your computer to an IP in the same subnet as the switch, e.g. 192.168.2.11 |
|||
* |
*Plug computer in to a port, e.g. port 7 |
||
| ⚫ | |||
*Plug computer in to a port, eg port 7 |
|||
| ⚫ | |||
| ⚫ | |||
| ⚫ | |||
| ⚫ | |||
| ⚫ | |||
*Enable HTTPS (Security - Secure Connection) generate certificate and apply |
*Enable HTTPS (Security - Secure Connection) generate certificate and apply |
||
== |
==Create VLANs== |
||
| ⚫ | |||
| ⚫ | |||
*Create 4 VLANs (VLANS - VLAN Configuration) |
*Create 4 VLANs (VLANS - VLAN Configuration) |
||
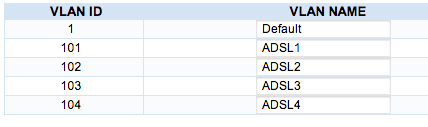
*Set the names to be ADSL1, ADSL2, ADSL3, ADSL4 - this will match the login/line numbers of the ADSL lines |
*Set the names to be ADSL1, ADSL2, ADSL3, ADSL4 - this will match the login/line numbers of the ADSL/FTTC lines |
||
[[File:1810G-8-VLANSList.png|border]] |
[[File:1810G-8-VLANSList.png|border]] |
||
==Configure ports for VLAN tagging |
==Configure ports for VLAN tagging== |
||
*Under VLANs - Participation Tagging |
*Under VLANs - Participation Tagging: |
||
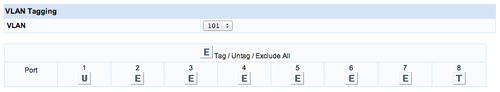
**set VLAN 101 to be U on port 1 and T on port 8. E on rest |
**set VLAN 101 to be U on port 1 and T on port 8. E on rest |
||
**set VLAN 102 to be U on port 2 and T on port 8. E on rest |
**set VLAN 102 to be U on port 2 and T on port 8. E on rest |
||
| Line 68: | Line 69: | ||
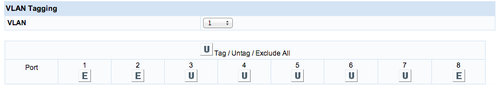
**set VLAN 1 to be E on port 1, 2, 3, 4 and U on port 5, 6, 7, 8 |
**set VLAN 1 to be E on port 1, 2, 3, 4 and U on port 5, 6, 7, 8 |
||
[[File:1810G-8-VLAN101.png]] |
[[File:1810G-8-VLAN101.png|border|500px]] |
||
[[File:1810G-8-VLAN1.png]] |
[[File:1810G-8-VLAN1.png|border|500px]] |
||
On some switches you may need to set the PVID accordingly - ie Port 1 = PVID 101, Port 2 = PVID 102 etc... This was needed on a PoE variant of a switch, but not on the non-PoE variant. |
|||
*SAVE CONFIG - otherwise you will learn the hard way |
*SAVE CONFIG - otherwise you will learn the hard way |
||
==IP Address== |
==IP Address== |
||
In order to access the Switch, we'll need to setup |
In order to access the Switch, we'll need to setup an interface on the FireBrick with a subnet in the same range as the switch. We can use the default 192.168.2.0/24, and this will be accessible from the LAN side. |
||
Alternately, we can use a public /30. This will involve a new /30 allocation on Clueless, routed to all the ADSL lines, and on the |
Alternately, we can use a public /30. This will involve a new /30 allocation on Clueless, routed to all the ADSL/FTTC lines, and on the FireBrick a subnet on the WAN interface. |
||
Set the gateway to the FireBrick, then the switch can access things like time server, syslog server etc... |
Set the gateway to the FireBrick, then the switch can access things like time server, syslog server etc... |
||
[[Category:FireBrick|Bonding]] |
|||
[[Category:Bonding Configuration]] |
|||
Latest revision as of 08:31, 22 May 2020
Overview
The FireBrick 2500/2700 have 4 ethernet ports, the 2900 has 4 plus an SFP which can be used with a Copper of fibre SFP to give an additional port. Typically one port will be for the LAN connection (for example - to the main office switch), and the rest for connections to the ADSL/FTTC modems.
As there are 4 ports are we restricted to only bonding up to 3 ADSL/FTTC lines? No.
To overcome the physical port restriction a VLAN switch can be used - for example:
ADSL MODEM 1 -- ADSL MODEM 2 -- ADSL MODEM 3 -- VLAN Switch -- Firebrick -- LAN SWITCH == Computers ADSL MODEM 4 --
The switch would be set up for 4 (or more) separate VLANs on the appropriate ports, and on the FireBrick, the <ppp .../> config would have VLAN="n".
VLAN Switch Config
Instructions on using a ZyXEL GS1900-8 switch: ZyXEL GS1900-8
Below are some notes on setting up a HP ProCurve 1810G-8:
The HP ProCurve 1810G-8 (J9449A) is a nice little 8 port managed switch. No fans and similar in size to a FireBrick.
Overview
The FireBrick will have a single WAN port, which will plug in to the HP Switch. The ADSL/FTTC modems will plug in to the HP Switch too. This will then, with VLANs, enable the FireBrick to use up to 7 ADSL/FTTC modems.
- Default IP is "192.168.2.10"
- Default username: admin
- Default password: 1234
Save Config
To make things a little easier, here is a saved config: File:FBVLANconfig1810G.bin.zip. It is the default config (default IP and password), but with VLANs as follows:
- Port 1 - VLAN 101, for ADSL line 1
- Port 2 - VLAN 102, for ADSL line 2
- Port 3 - VLAN 103, for ADSL line 3
- Port 4 - VLAN 104, for ADSL line 4
- Port 8 is for the FireBrick
The config was from HP ProCurve 1810G - 8 GE, P.1.17, eCos-2.0, Software Version, P.1.17
However it only takes a few minutes to set up the VLANs manually as follows:
Basic Settings
- Set your computer to an IP in the same subnet as the switch, e.g. 192.168.2.11
- Plug computer in to a port, e.g. port 7
- Log in to http://192.168.2.10 with a blank password
- Maybe set the system description details
- Set admin password (Maintenance - Password Manager) then save and re-login
- Enable HTTPS (Security - Secure Connection) generate certificate and apply
Create VLANs
We will set ports 1-4 to be VLANs 101, 102, 103, 104. We'll use port 8 for plugging in to the FireBrick, and use port 7 for our admin.
- Create 4 VLANs (VLANS - VLAN Configuration)
- Set the names to be ADSL1, ADSL2, ADSL3, ADSL4 - this will match the login/line numbers of the ADSL/FTTC lines
Configure ports for VLAN tagging
- Under VLANs - Participation Tagging:
- set VLAN 101 to be U on port 1 and T on port 8. E on rest
- set VLAN 102 to be U on port 2 and T on port 8. E on rest
- set VLAN 103 to be U on port 3 and T on port 8. E on rest
- set VLAN 104 to be U on port 4 and T on port 8. E on rest
- set VLAN 1 to be E on port 1, 2, 3, 4 and U on port 5, 6, 7, 8
On some switches you may need to set the PVID accordingly - ie Port 1 = PVID 101, Port 2 = PVID 102 etc... This was needed on a PoE variant of a switch, but not on the non-PoE variant.
- SAVE CONFIG - otherwise you will learn the hard way
IP Address
In order to access the Switch, we'll need to setup an interface on the FireBrick with a subnet in the same range as the switch. We can use the default 192.168.2.0/24, and this will be accessible from the LAN side. Alternately, we can use a public /30. This will involve a new /30 allocation on Clueless, routed to all the ADSL/FTTC lines, and on the FireBrick a subnet on the WAN interface. Set the gateway to the FireBrick, then the switch can access things like time server, syslog server etc...