IPsec ZyXEL USG40: Difference between revisions
No edit summary |
|||
| Line 30: | Line 30: | ||
* The "Authentication" section needs to be set to "Pre-shared Key" - This is the pass phrase that you have set on the FireBrick. |
* The "Authentication" section needs to be set to "Pre-shared Key" - This is the pass phrase that you have set on the FireBrick. |
||
<gallery> |
|||
Zywall4.png| |
|||
</gallery> |
|||
* "Local ID type" needs to be set to "DNS". In the "Content" box, you should enter the domain name for your FireBrick. e.g. "internal2.**.co.uk". |
* "Local ID type" needs to be set to "DNS". In the "Content" box, you should enter the domain name for your FireBrick. e.g. "internal2.**.co.uk". |
||
| Line 43: | Line 45: | ||
Now, click "OK" and activate the config by clicking on the entry that you have just created and pressing the "Activate" button. |
Now, click "OK" and activate the config by clicking on the entry that you have just created and pressing the "Activate" button. |
||
<gallery> |
|||
Zywall5.png| |
|||
</gallery> |
|||
<br> |
<br> |
||
Next, we're going to select the "VPN Connection" Tab and click "Add". |
Next, we're going to select the "VPN Connection" Tab and click "Add". |
||
<gallery> |
|||
Zywall6.png| |
|||
</gallery> |
|||
* Click show "Advanced settings" |
* Click show "Advanced settings" |
||
* Select "Nailed-Up" and "Enable Replay Detection". |
* Select "Nailed-Up" and "Enable Replay Detection". |
||
<gallery> |
|||
Zywall6.png| |
|||
</gallery> |
|||
* Under "VPN Gateway" select "Remote Access (Client Role) and select the VPN Gateway you just created in the drop down box. |
* Under "VPN Gateway" select "Remote Access (Client Role) and select the VPN Gateway you just created in the drop down box. |
||
* in "Local Policy" select "DMZ_SUBNET" and in "Remote Policy" select "LAN1_SUBNET". |
* in "Local Policy" select "DMZ_SUBNET" and in "Remote Policy" select "LAN1_SUBNET". |
||
<gallery> |
|||
Zywall8.png| |
|||
</gallery> |
|||
* Under "Phase 2 Setting", change the "SA Life Time" to "3000000". |
* Under "Phase 2 Setting", change the "SA Life Time" to "3000000". |
||
| Line 60: | Line 72: | ||
* In the "Proposal" section, change "Encryption" to "3DES" and the "Authentication" to "SHA1". |
* In the "Proposal" section, change "Encryption" to "3DES" and the "Authentication" to "SHA1". |
||
* We then need to change the "Perfect Forward Secrecy (PFS)" to "DH2". |
* We then need to change the "Perfect Forward Secrecy (PFS)" to "DH2". |
||
<gallery> |
|||
Zywall9.png| |
|||
</gallery> |
|||
* Now all we need to do is click "OK" and "Activate". |
* Now all we need to do is click "OK" and "Activate". |
||
<gallery> |
|||
Zywall10.png| |
|||
</gallery> |
|||
<br> |
<br> |
||
Once all of this has been done, press "Connect" and you should see that you now have an active IPsec connection from your ZyWALL USG40 to your FireBrick. |
Once all of this has been done, press "Connect" and you should see that you now have an active IPsec connection from your ZyWALL USG40 to your FireBrick. |
||
<gallery> |
|||
Zywall11.png| |
|||
</gallery> |
|||
Revision as of 12:11, 20 July 2015
FireBrick IPsec
Please make sure you have followed the following tutorial on how to set up an IPSec tunnel on a FireBrick: https://support.aa.net.uk/FireBrick_to_FireBrick_IPsec_(Howto)
Note: Version 4 of ZyXELs firmware is required, version 3 does not support IKEv2. A copy of the Firmware is available here: ftp://ftp2.zyxel.com/USG40/firmware/USG40_4.11(AALA.2)C0.zip
ZyWALL USG40 IPsec instructions
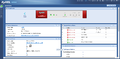
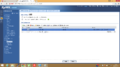
- Log into the ZyWALL Dashboard.
- Enter the configuration tab on the left & select "VPN" and then select "IPsec VPN" (sic).
- Select the "VPN Gateway" tab.
- Click on "Add".
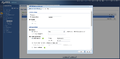
- Select "Show Advanced Settings".
- Make sure that you have ticked the "Enable" box for the connection.
- Enter a VPN Gateway name, for example my FireBrick is called "Internal2", so that's the name I will use for this configuration.
- Select IKEv2 protocol.
- Keep "My Address" as "Wan1" or select one that suits your specific configuration.
- Under "Peer Gateway Address" select "Static Address" and enter the public IP Address of your FireBrick. - Note, keep "Secondary" as "0.0.0.0".
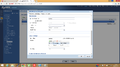
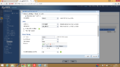
- The "Authentication" section needs to be set to "Pre-shared Key" - This is the pass phrase that you have set on the FireBrick.
- "Local ID type" needs to be set to "DNS". In the "Content" box, you should enter the domain name for your FireBrick. e.g. "internal2.**.co.uk".
- "Peer ID type" should be set as "Any".
- The "SA Life Time" field should have a value of "3000000" Seconds.
Now, the Proposal that the USG should be sending to the FireBrick is as follows:
- '#1' - "Encryption: "3DES" - Authentication: "SHA1" and the key group should be set as "DH2".
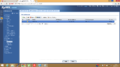
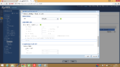
Now, click "OK" and activate the config by clicking on the entry that you have just created and pressing the "Activate" button.
Next, we're going to select the "VPN Connection" Tab and click "Add".
- Click show "Advanced settings"
- Select "Nailed-Up" and "Enable Replay Detection".
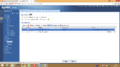
- Under "VPN Gateway" select "Remote Access (Client Role) and select the VPN Gateway you just created in the drop down box.
- in "Local Policy" select "DMZ_SUBNET" and in "Remote Policy" select "LAN1_SUBNET".
- Under "Phase 2 Setting", change the "SA Life Time" to "3000000".
- Keep the defaults fror "Active Protocol" & "Encapsulation".
- In the "Proposal" section, change "Encryption" to "3DES" and the "Authentication" to "SHA1".
- We then need to change the "Perfect Forward Secrecy (PFS)" to "DH2".
- Now all we need to do is click "OK" and "Activate".
Once all of this has been done, press "Connect" and you should see that you now have an active IPsec connection from your ZyWALL USG40 to your FireBrick.