FireBrick IPsec Tunnel with Manual Keys (Deprecated): Difference between revisions
No edit summary |
No edit summary |
||
| Line 23: | Line 23: | ||
|Just a name so as to create a CQM graph |
|Just a name so as to create a CQM graph |
||
|- |
|- |
||
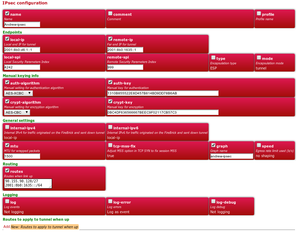
!local-ip |
|||
|Our FireBrick IP to use as the source |
|Our FireBrick IP to use as the source |
||
|- |
|- |
||
!remote-ip |
|||
|Remote FireBrick IP |
|Remote FireBrick IP |
||
|- |
|- |
||
!local-spi |
|||
| |
| |
||
|- |
|- |
||
!remote-spi |
|||
| |
| |
||
|- |
|- |
||
!auth-algorithm |
|||
| |
| |
||
|- |
|- |
||
!auth-key |
|||
| |
| |
||
|- |
|- |
||
!crypt-algorithm |
|||
| |
| |
||
|- |
|- |
||
!crypt-key |
|||
| |
| |
||
|- |
|- |
||
!routes |
|||
|IP blocks to route through the tunnel - ie LAN IPs of the other end |
|IP blocks to route through the tunnel - ie LAN IPs of the other end |
||
|} |
|} |
||
Revision as of 11:06, 28 June 2013
FireBrick to FireBrick
Here we will create a tunnel between 2 firebricks, Paul and Andrew. We will then set routing to route each others LAN blocks though the Tunnel. As the 2 endpoints have IPv6, we'll establish the tunnel over IPv6.
Side A Config
<ipsec name="Andrew-ipsec" mtu="1500" graph="andrew-ipsec" local-ip="2001:8b0:d6:1::1" remote-ip="2001:8b0:1635::1" local-spi="4242" remote-spi="999" auth-algorithm="AES-XCBC" auth-key="1310B855522E8D457B814BD9DD78B6AB" crypt-algorithm="AES-CBC" crypt-key="0BC4DF636566667BEEC9F02117CB57C3" routes="90.155.90.128/27 2001:8b0:1635::/64"/>
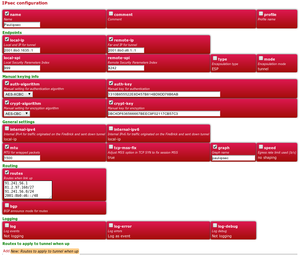
| IPSec settings overview | |
|---|---|
| name | Just a name for this Tunnel |
| mtu | |
| graph | Just a name so as to create a CQM graph |
| local-ip | Our FireBrick IP to use as the source |
| remote-ip | Remote FireBrick IP |
| local-spi | |
| remote-spi | |
| auth-algorithm | |
| auth-key | |
| crypt-algorithm | |
| crypt-key | |
| routes | IP blocks to route through the tunnel - ie LAN IPs of the other end |
name="Andrew-ipsec" mtu="1500" graph="andrew-ipsec" local-ip="2001:8b0:d6:1::1" remote-ip="2001:8b0:1635::1" local-spi="4242" remote-spi="999" auth-algorithm="AES-XCBC" auth-key="1310B855522E8D457B814BD9DD78B6AB" crypt-algorithm="AES-CBC" crypt-key="0BC4DF636566667BEEC9F02117CB57C3" routes="90.155.90.128/27 2001:8b0:1635::/64"/>
Side B Config
<ipsec name="Paul-ipsec" mtu="1500" graph="paul-ipsec" local-ip="2001:8b0:1635::1" remote-ip="2001:8b0:d6:1::1" local-spi="999" remote-spi="4242" auth-algorithm="AES-XCBC" auth-key="1310B855522E8D457B814BD9DD78B6AB" crypt-algorithm="AES-CBC" crypt-key="0BC4DF636566667BEEC9F02117CB57C3" routes="91.241.56.1 81.2.97.160/27 91.241.56.0/24 2001:8b0:d6::/48"/>
Testing
These 2 FireBricks both happen to be on AAISP FTTC lines, and a normal traceroute would go via the AAISP router, but when the IPSec tunnel is enabled the traceroute goes direct.
Traceroute Before:
$ traceroute 91.241.56.1 traceroute to 91.241.56.1 (91.241.56.1), 30 hops max, 60 byte packets 1 brick.h.hearn.org.uk (90.155.90.129) 0.344 ms 0.321 ms 0.310 ms 2 a.gormless.thn.aa.net.uk (90.155.53.51) 11.703 ms 11.712 ms 11.834 ms 3 brick.shibboleet.ltd.uk (91.241.56.1) 24.862 ms 24.871 ms 25.251 ms
Traceroute After:
$ traceroute 91.241.56.1 traceroute to 91.241.56.1 (91.241.56.1), 30 hops max, 60 byte packets 1 brick.h.hearn.org.uk (90.155.90.129) 0.358 ms 0.342 ms 0.329 ms 2 brick.shibboleet.ltd.uk (91.241.56.1) 26.178 ms 26.861 ms 27.123 ms