L2TP Overview: Difference between revisions
m →Notes: clean up, typos fixed: eg → e.g. |
|||
| Line 1: | Line 1: | ||
=Notes= |
=Notes= |
||
*AAISP Data SIMs can be relayed on to your L2TP server |
*AAISP Data SIMs can be relayed on to your '''L2TP''' server |
||
*AAISP DSL lines can be relayed on to your L2TP server -this isn't a usual configuration as customers normally want us to do all the work, but it is possible. |
*AAISP DSL lines can be relayed on to your L2TP server -this isn't a usual configuration as customers normally want us to do all the work, but it is possible. |
||
*On special request you can have an L2TP login in to AAISP - pricing is based on the usage, and is currently priced the same as usage costs on AAISP 'Be' lines. |
*On special request you can have an L2TP login in to AAISP - pricing is based on the usage, and is currently priced the same as usage costs on AAISP 'Be' lines. |
||
*Also see [[FireBrick L2TP Server]] regarding the FireBrick being an L2TP 'server' - |
*Also see [[FireBrick L2TP Server]] regarding the FireBrick being an L2TP 'server' - e.g. for Data SIMs to connect to. |
||
*From March 2014 we are now emailing and tweeting when an L2TP line goes up or down unexpectedly. Settings for this are on the control page. This works in the same way as the up/down messages we send for broadband lines. |
*From March 2014 we are now emailing and tweeting when an L2TP line goes up or down unexpectedly. Settings for this are on the control page. This works in the same way as the up/down messages we send for broadband lines. |
||
Revision as of 21:20, 6 January 2015
Notes
- AAISP Data SIMs can be relayed on to your L2TP server
- AAISP DSL lines can be relayed on to your L2TP server -this isn't a usual configuration as customers normally want us to do all the work, but it is possible.
- On special request you can have an L2TP login in to AAISP - pricing is based on the usage, and is currently priced the same as usage costs on AAISP 'Be' lines.
- Also see FireBrick L2TP Server regarding the FireBrick being an L2TP 'server' - e.g. for Data SIMs to connect to.
- From March 2014 we are now emailing and tweeting when an L2TP line goes up or down unexpectedly. Settings for this are on the control page. This works in the same way as the up/down messages we send for broadband lines.
L2TP Relay Configuration Options at AAISP Side
L2TP setting are set by staff, so please do contact them for any changes or setup. The information that would be requested is:
- Target IP (with an optional backup IP) - the L2TP server at your side
- Host - the hostname we present
- Secret - the password we use (optional)
Some Notes from customers setting up L2TP IN to AAISP:
FireBrick FB2500/2700 Fully Loaded
The FireBrick can connect as an L2TP client for fallback and for its main connection. One thing to watch out for is making sure that the FB doesn't set its own gateway to be the tunnel (which would logically send tunnel packets up the tunnel, which is horrid). You can get around this by using separate routing tables.
This example is for L2TP being the main connection:
<interface name="WAN"
port="WAN1"
table="1"
comment="DHCP client">
<l2tp>
<outgoing name="AAISP"
ip="90.155.53.19"
graph="AAISP"
table="1"
payload-table="0"
username="example@a"
password="secret"
tcp-mss-fix="true"
comment="L2TP tunnel to AAISP"/>
</l2tp>
You can set to fall back to NAT if the tunnel is down. Traffic on routing table 0 won't have a default gateway if the L2TP is down, so will match this rule set that has target interface "nowhere":
<rule-set name="Fallback"
target-interface="nowhere"
no-match-action="continue"
comment="NAT fallback if can't establish L2TP">
<rule name="NAT"
set-nat="true"
set-table="1"
action="accept"/>
</rule-set>
If the L2TP is being used for fallback, you are probably better off setting the routing table for the L2TP to something other than 0. Remember firewall rules only apply to single routing tables.
RouterBoard
Connecting to L2TP with a RouterBoard was pretty seamless - put in the L2TP server IP, username and password and it just connects. Have to mess about with IP / Route and NAT / masquerading a bit to get devices behind the RouterBoard online but that all depends on whether you have an additional IP block and what you want to do with it anyway.
Apple OSX
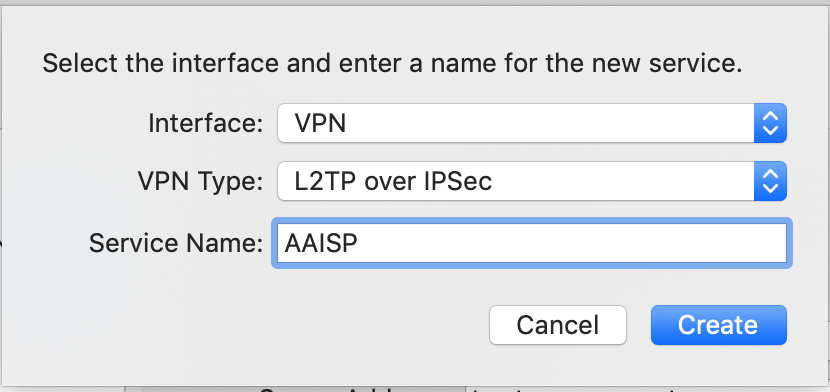
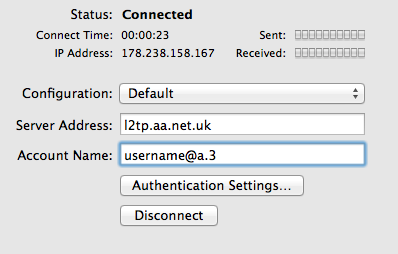
An Apple computer can be used to create an L2TP connection in to AAISP, here's how:
- Apple Menu - Settings - Network
- Click the + Icon
- Create a new VPN Interface with Type L2TP over IPSec
- In the Authentication settings set the Password
- For ease of use Tick 'Show VPN status in menu bar
- Optionally, in the Advanced Settings Tick, 'Send all Traffic over VPN connection'
- Then Connect
- To Disconnect, click Disconnect
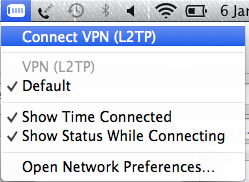
You can use the new icon in the Status bar (Up by the clock, to connect and disconnect the connection
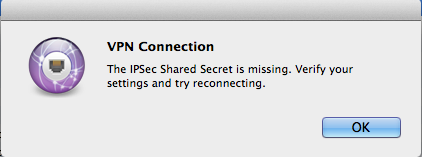
VPN Connection - IPsec Error
Use this at your own risk. The notes below involves editing/creating system files, and whilst 'worked for us' may not work for you.
By default, OSX requires the L2TP connection to use IPSec encryption. At the moment the AAISP service is just plain L2TP and does not offer encryption.
To enable OSX to connect without IPSec, then the /etc/ppp/options file needs to be edited. A simple way of doing this is as follows:
- Use the Search icon to search for Terminal
and then enter in:
echo "plugin L2TP.ppp" > options echo "l2tpnoipsec" >> options sudo mv options /etc/ppp
If the mv (move) fails, then you may already have a /etc/ppp/options file, in this case it would need to be edited manually.
To undo this change delete the /etc/ppp/options file.
Windows 7
Connecting with Windoze 7 was almost as easy except that the default connection settings don't work. You have to edit the connection properties and on the Security tab change 'Type of VPN:' to 'Layer 2 Tunneling Protocol with IPsec (L2TP/IPSec)' otherwise it only tries PPTP, and change 'Data encryption:' to 'Optional encryption (connect even if no encryption)' as it doesn't like A+A's certificate (because RevK declines to use a root certification authority recognised by Microsoft, or is it that Microsoft declines to recognise the root certification authority chosen by RevK). I guess the alternative would probably be to add the root certificate to the machine in question. Anyway, with those two changes it works fine.
Watch out if you are using IPv6. It seems that Win7 negotiates a non-routable IPv6 address with the LNS. You have to discard this address and manually configure one of your routed IPv6 addresses. ipconfig /release6 is your friend here.
Cisco Routers
Cisco routers running IOS 12.3(2)T and later support L2TP client initiated tunneling which allows the router to establish an L2TP tunnel to A&A's L2TP server.
Most of the information required was gleaned from here: [1] plus a bit of trial and error and some packet capturing of good and bad L2TP sessions.
I have tested this on a Cisco 837 router running 12.3(11)YZ2, a 2821 running 12.4(15)T10 SPServices and a 2801 running 12.4(24)T3 ADVIPServices
Caveats:
- You will need to sanity check routing in your particular environment. This is especially important if you choose to use ppp ipcp route default on the l2tp tunnel. It's safest to make sure that you have a static route set to the L2TP server.
- I haven't tested this for IPV6 yet.
- This is "early release" information - I haven't yet used this in anger over a long period of time but will try to remember to come back and update if I find any major issues.
- This config snippet contains no security settings - be sure to configure some!
- I've used the IP address of the L2TP server rather than the DNS address - this is obviously at risk of change .
- You need to be running IP CEF on the router
Config:
Replace <whatever> with the appropriate information for your connection
ip cef l2tp-class lc-aaisp pseudowire-class pc-aaisp encapsulation l2tpv2 protocol l2tpv2 lc-aaisp ip local interface <interface that l2tp connection should go out from> interface Virtual-PPP9797 shutdown ip address negotiated no cdp enable ppp authentication chap callin ppp chap hostname <l2tp line login eg stzzz@a.2> ppp chap password 0 <site password> ppp direction callout ppp pap refuse pseudowire 90.155.53.19 10 pw-class pc-aaisp
Once the interface is configured you can issue a no shut on it to bring it up.
Debugging:
debug ppp authentication and debug ppp negotiation are your friends... In particular if you see "Circuit ID not set - contact support" in the authentication debug, contact A&A support to get them to fix your L2TP login.
Once the connection is up, you should see the virtual PPP interface configured with the static IP that is assigned to it in clueless.
If you get stuck, pop into the IRC channel and see if I'm around (basil_uk) and I'll help if possible.
Other Hardware
The TL-WR741ND router works, although it can only do NAT, but is very cheap.